
発見したマルウェアの情報(サマリー)
*) For the English analysis I dumped all text in pastebin ( http://pastebin.com/s5mnVNdK )
■下記のサイト↓
diybbb.com (IPアドレス:106.187.46.93)
■下記のダウンロードURL/ファイル↓
hxxp://diybbb.com/update.exe
(証拠↓)
■下記のマルウェアを発見しました↓
■オンラインスキャン結果↓
diybbb.com (IPアドレス:106.187.46.93)
■下記のダウンロードURL/ファイル↓
hxxp://diybbb.com/update.exe
(証拠↓)
Sat Jan 28 20:37:20 JST 201
--20:37:04-- hxxp://diybbb.com/update.exe
=> `update.exe.1'
Resolving diybbb.com... 106.187.46.93
Connecting to diybbb.com|106.187.46.93|:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 870,186 (850K) [application/octet-stream]
100%[====================================>] 870,186 1.49M/s
20:37:05 (1.49 MB/s) - `update.exe.1' saved [870186/870186]■下記のマルウェアを発見しました↓
マルウェア種類:Trojan (トロイ木馬)
マルウェア名 :Trojan-Downloader.Win32.FlyStudioの新種類
マルウェア機能:Dropper, Backdoor, Downloader
説明 :感染されたパソコンにマルウェアファイルが展開(Dropper)、
UDPとHTTP経由でリモート側のIPを接続(Backdoor)
リモートサイトからダウンロード依頼を投げる(Downloader)■オンラインスキャン結果↓
Detection ratio : 25 / 42 Analysis date : 2012-01-28 12:44:03 UTC SHA256 : 84a6adc0975102ca72cdebcf28f9d962d13742aad5980483ded1e38e93162392
※詳細説明は以下になります
■マルウェアのファイル(バイナリー調査)
ファイル名:update.exe サイズ :849.8 KB ( 870,186 bytes ) MD5 : 8eef0a7b25c397a3c14179563c8a0f49 First Detected: 2011-12-05 Last Detected: 2012-01-28 アイコンの通り、実行(PE)ファイルですね (実行フラグ@IMAGE_SCN_MEM_WRITE & IMAGE_SCN_MEM_EXECUTEが設定された) アイコンとプロパティ: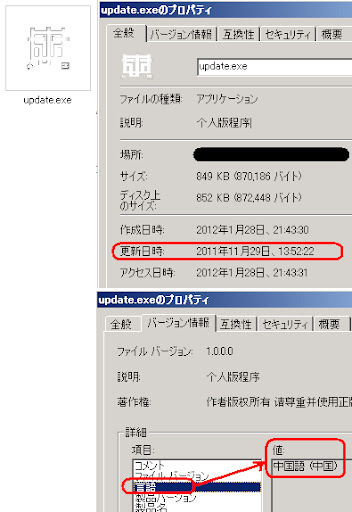
■ 調査結果 - 本サンプルのあやしいポイント↓ 1. 書いたCRCと本当のCRC情報が違う: Claimed: 0 ; Actual: 899,309 (packerのせい) 2. 日付け(timestamp)が古過ぎます : 0x59BFFA3 [Mon Dec 25 05:33:23 1972 UTC 3. Compile Timeが古過ぎて: 1972-12-25 14:33:23 4. 元はMicrosoft Visual Cでcompileされた物ですが、その後にあやしいpackerを使ったそうです packer種類 : Installer VISE Custom 5. あやしいentropi: IMAGE_SECTION_HEADER Entropy: 7.7067096641 [IMAGE_SECTION_HEADER] Name: .data Misc: 0x23000 Misc_PhysicalAddress: 0x23000 Misc_VirtualSize: 0x23000 VirtualAddress: 0x9000 SizeOfRawData: 0x23000 PointerToRawData: 0x9000 PointerToRelocations: 0x0 PointerToLinenumbers: 0x0 NumberOfRelocations: 0x0 NumberOfLinenumbers: 0x0 Characteristics: 0xE0000040 6. 書いたDLLのコールの中にあやしいコールが沢山発見↓ OriginalFirstThunk: 0x6690 Name: 0x67EA FirstThunk: 0x6000 KERNEL32.dll.GetProcAddress Hint[318] <--- Anti Debugging traces KERNEL32.dll.LoadLibraryA Hint[450] <---- Anti Debugging traces KERNEL32.dll.CloseHandle Hint[27] <-----Anti Debugging traces KERNEL32.dll.WriteFile Hint[735] KERNEL32.dll.CreateDirectoryA Hint[45] <----- Why has to create a folder? KERNEL32.dll.GetTempPathA Hint[357] KERNEL32.dll.ReadFile Hint[536] KERNEL32.dll.SetFilePointer Hint[618] KERNEL32.dll.CreateFileA Hint[52] <------ Why has to create a file? KERNEL32.dll.GetModuleFileNameA Hint[292] KERNEL32.dll.GetStringTypeA Hint[339] KERNEL32.dll.LCMapStringW Hint[448] KERNEL32.dll.LCMapStringA Hint[447] KERNEL32.dll.HeapAlloc Hint[409] KERNEL32.dll.HeapFree Hint[415] KERNEL32.dll.GetModuleHandleA Hint[294] KERNEL32.dll.GetStartupInfoA Hint[336] KERNEL32.dll.GetCommandLineA Hint[202] <--- Why need to run a command line? KERNEL32.dll.GetVersion Hint[372] KERNEL32.dll.ExitProcess Hint[125] KERNEL32.dll.HeapDestroy Hint[413] KERNEL32.dll.HeapCreate Hint[411] <---- DEP setting change trace KERNEL32.dll.VirtualFree Hint[703] <---- DEP setting change trace KERNEL32.dll.VirtualAlloc Hint[699] <---- DEP setting change trace KERNEL32.dll.HeapReAlloc Hint[418] <---- DEP setting change trace KERNEL32.dll.TerminateProcess Hint[670] <---Why has to terminate a process? which? KERNEL32.dll.GetCurrentProcess Hint[247] <-----Anti Debugging traces KERNEL32.dll.UnhandledExceptionFilter Hint[685] KERNEL32.dll.FreeEnvironmentStringsA Hint[178] KERNEL32.dll.FreeEnvironmentStringsW Hint[179] KERNEL32.dll.WideCharToMultiByte Hint[722] KERNEL32.dll.GetEnvironmentStrings Hint[262] KERNEL32.dll.GetEnvironmentStringsW Hint[264] KERNEL32.dll.SetHandleCount Hint[621] KERNEL32.dll.GetStdHandle Hint[338] KERNEL32.dll.GetFileType Hint[277] KERNEL32.dll.RtlUnwind Hint[559] KERNEL32.dll.GetCPInfo Hint[191] KERNEL32.dll.GetACP Hint[185] KERNEL32.dll.GetOEMCP Hint[305] KERNEL32.dll.MultiByteToWideChar Hint[484] KERNEL32.dll.GetStringTypeW Hint[342] USER32.dll.MessageBoxA Hint[446] USER32.dll.wsprintfA Hint[684] 上記のあやしいDLLコールのアドレス↓ 0x406000 GetProcAddress 0x406004 LoadLibraryA 0x406008 CloseHandle 0x406068 GetCurrentProcess 0x406020 CreateFileA 0x406054 HeapCreate 0x40605c VirtualAlloc 7. バイナリーの中にまた別のあやしいバイナリーを転回する積もり…↓
テキストは↓ 0000000090B8 0000004090B8 0 krnln 0000000090BE 0000004090BE 0 d09f2340818511d396f6aaf844c7e325 0000000090F2 0000004090F2 0 EThread 0000000090FA 0000004090FA 0 5F99C1642A2F4e03850721B4F5D7C3F8 000000009131 000000409131 0 A512548E76954B6E92C21055517615B0 000000009165 000000409165 0 shell 00000000916B 00000040916B 0 52F260023059454187AF826A3C07AF2A 0000000091A7 0000004091A7 0 iext6 0000000091AD 0000004091AD 0 {E60056EA-07A8-4bf5-B6F0-DF05DE6FAE1F} 8. さくっとオンラインスキャンしたら、マルウェアの結果が沢山出ました↓ Detection ratio : 25 / 42 Analysis date : 2012-01-28 12:44:03 UTC SHA256 : 84a6adc0975102ca72cdebcf28f9d962d13742aad5980483ded1e38e93162392 ----------------------------------------------------------------------- アンリウイルスメーカ // マルウェア検知結果 // 最新版ウイルスDBの日付け ----------------------------------------------------------------------- AhnLab-V3 Win32/Flystudio.worm.Gen 20120127 AntiVir - 20120127 Antiy-AVL - 20120128 Avast - 20120128 AVG BackDoor.FlyAgent.D 20120128 BitDefender - 20120128 ByteHero - 20120126 CAT-QuickHeal Win32.Trojan-Dropper.VBS.p.5 20120127 ClamAV Trojan.Agent-64034 20120128 Commtouch W32/FlyStudio.A.gen!Eldorado 20120128 Comodo TrojWare.Win32.Agent.pkd 20120128 DrWeb - 20120128 Emsisoft Trojan-Dropper.Win32.Binder!IK 20120128 eSafe Win32.TrojanAgent.Dq 20120126 eTrust-Vet Win32/SillyAutorun.ALB 20120127 F-Prot W32/FlyStudio.A.gen!Eldorado 20120127 F-Secure Trojan:W32/Agent.DQOD 20120128 Fortinet W32/BDoor.DRV!tr 20120128 GData - 20120128 Ikarus Trojan-Dropper.Win32.Binder 20120128 Jiangmin - 20120127 K7AntiVirus Riskware 20120127 Kaspersky - 20120128 McAfee BackDoor-DRV.gen.c 20120127 McAfee-GW-Ed. BackDoor-DRV.gen.c 20120128 Microsoft - 20120128 NOD32 Win32/FlyStudio.OHX 20120128 Norman W32/Suspicious_Gen2.RZVIX 20120127 nProtect - 20120128 Panda Trj/CI.A 20120128 PCTools - 20120128 Rising - 20120118 Sophos Troj/Agent-OKI 20120128 SUPERAntiSpyWr - 20120128 Symantec WS.Reputation.1 20120128 TheHacker Trojan/Downloader.Flystudio.gen 20120127 TrendMicro TROJ_SPNR.15A912 20120128 Trend-HouseCall TROJ_SPNR.0BLQ11 20120128 VBA32 - 20120126 VIPRE Trojan.Win32.Autorun.dm (v) 20120128 ViRobot - 20120128 VirusBuster - 20120127 上記の結果を見た所、新種類のトロイですので、 まだサンプルが貰って無いAVメーカーが多いですね。 ちゃんとサンプルが貰ったメーカーがはっきりマルウェアの聡明が出したみたいです。
■マルウェア行動分析調査結果
1. 起動した時に下記のDLLをロードされて
C:\WINDOWS\system32\ntdll.dll 0x7C900000 0x000AF000
C:\WINDOWS\system32\kernel32.dll 0x7C800000 0x000F6000
C:\WINDOWS\system32\USER32.dll 0x7E410000 0x00091000
C:\WINDOWS\system32\GDI32.dll 0x77F10000 0x00049000
2. 起動されたらRUN-TIMEのDLLがこんな感じ↓
C:\DOC~\..1\Temp\E_N4\krnln.fnr 0x10000000 0x0011A000
C:\WINDOWS\system32\COMCTL32.dll 0x5D090000 0x0009A000
C:\WINDOWS\system32\OLEPRO32.DLL 0x5EDD0000 0x00017000
C:\WINDOWS\system32\WS2HELP.dll 0x71AA0000 0x00008000
C:\WINDOWS\system32\WS2_32.dll 0x71AB0000 0x00017000
C:\WINDOWS\system32\WINSPOOL.DRV 0x73000000 0x00026000
C:\WINDOWS\system32\DCIMAN32.DLL 0x73BC0000 0x00006000
C:\WINDOWS\system32\MSCTF.dll 0x74720000 0x0004C000
3. 下記のフォルダーをパソコンに作ってくれて↓
%Temp% \E_N4
%System% \13E92A\
4. 下記のファイルをパソコンに作ってくれました(DROP)↓
%Temp% \E_N4
%Temp% \E_N4\EThread.fne (Malware apps Interface)
%Temp% \E_N4\iext6.fne
%Temp% \E_N4\krnln.fnr (Malware kernel support library)
%Temp% \E_N4\shell.fne (Malware shell support library)
%Temp% \E_N4\spec.fne
5. 下記のファイルをシステムのフォルダーにコーピーされて↓
%System%\ 13E92A\EThread.fne
%System%\ 13E92A\iext6.fne
%System%\ 13E92A\krnln.fnr
%System%\ 13E92A\shell.fne
%System%\ 13E92A\spec.fne
6. Windowsのレジストリーには追加されて↓
HKU\S-1-5-21-842925246-1425521274-308236825-500\Software\Microsoft\Multimedia\DrawDib
===> vga.drv 800x600x16(565 0) 31,31,31,31
7. 下記のネットワーク動きを発見しました↓
IP ポート情報
173.252.216.29 80
96.44.133.98 80 (HTTPですね)
リクエスト情報をトラップしたら下記のURLを発見↓
HTTP/1.1 ⇒ GET
hxxp://www.aikest.com/reg.asp?a=5331
hxxp://www.chuangqilm.com/iclk/?zoneid=7887&uid=5331
8. DROPされたマルウェア・ファイルのレピュテーション調査結果↓
%Temp%\E_N4\EThread.fne (previous sample: internet.fne)
%System%\13E92A\EThread.fne
Size: 184,320 bytes
MD5: 0xC93E19032EFD345023E240A0E9F570BA
SHA-1: 0xBC7AD7302513317F3C8663FAC8328A9DA588252D
Verdict:
Trojan.Galapoper [PCTools]
Trojan.Galapoper.A [Symantec]
Tool-EPLLib.gen.b [McAfee]
Mal/EncPk-NB [Sophos]
possible-Threat.HackTool.EPLLib [Ikarus]
packed with PE-Crypt.CF [Kaspersky Lab]
%Temp%\E_N4\krnln.fnr
%System%\13E92A\krnln.fnr
Size: 701,824 bytes
MD5: 0x6E32451019FDB76AB888F6FB5F5836E0
SHA-1: 0xF9E495276C9AD994DDBE0D1716F37081266273A9
Verdict:
Trojan.Gen [PCTools]
Trojan.Gen [Symantec]
Mal/EncPk-NB [Sophos]
Trojan.Win32.Gendal [Ikarus]
packed with PE-Crypt.CF [Kaspersky Lab]
%Temp%\E_N4\shell.fne
%System%\13E92A\shell.fne
Size: 40,960 bytes
MD5: 0xA82A3F811F1A01C9EEBF7E76C8C3CD6C
SHA-1: 0x96C026497D308450E460F058E3B0B68D75C0684A
Verdict:
Trojan.Generic [PCTools]
Trojan Horse [Symantec]
Generic PWS.y!hv.s [McAfee]
Mal/EncPk-NB [Sophos]
Trojan:Win32/Orsam!rts [Microsoft]
Trojan.Peed [Ikarus]
Win-Trojan/Xema.variant [AhnLab]
packed with PE-Crypt.CF [Kaspersky Lab]
%Temp%\E_N4\spec.fne
%System%\13E92A\spec.fne
Size: 73,728 bytes
MD5: 0x2C6AECDD5D8D812C5BF1D678252B1901
SHA-1: 0x65976048B550BDE89CEC8B45CF40060688C96A12
Verdict:
Trojan.Generic [PCTools]
Trojan Horse [Symantec]
Vundo.gen.cg [McAfee]
Mal/EncPk-NB [Sophos]
Trojan:Win32/Trabin!rts [Microsoft]
Trojan.Peed [Ikarus]
Win-Trojan/Xema.variant [AhnLab]
packed with PE-Crypt.CF [Kaspersky Lab]■マルウェアのソース調査結果(ネットワーク/IP/DNS/登録/など…)↓
1. 感染されたウェブサイトのドメイン登録情報↓ ドメイン登録情報 Domain Name: DIYBBB.COM Registrar: XIN NET TECHNOLOGY CORPORATION Whois Server: whois.paycenter.com.cn Referral URL: http://www.xinnet.com Name Server: F1G1NS1.DNSPOD.NET Name Server: F1G1NS2.DNSPOD.NET Status: ok Updated Date: 24-dec-2011 Creation Date: 28-aug-2010 Expiration Date: 28-aug-2013 Cross Check: Domain Name : diybbb.com PunnyCode : diybbb.com Creation Date : 2010-08-29 11:00:42 Updated Date : 2011-12-25 10:27:26 Expiration Date : 2013-08-29 11:00:39 Administrative /Technical/Billing Contact: Name : LIN YAN Organization : LIN YAN Address : TIANHE QU BUYNOW C1507 City : GuangZhou Province/State : Guangdong Country : CN Postal Code : 510000 Phone Number : 86-020-62683253 Fax : 86-020-62683286 Email : mimidi@126.com インターネット・ルーティング情報(図)インターネット・ルーティング情報・IDCとAS情報
2. 感染されたウェブサイトのIPアドレス登録情報 IP ADDRESS : 106.187.46.93 REVERSE DNS: 93.46.187.106.in-addr.arpa domain name pointer li389-93.members.linode.com. ASNumber : 2516 Prefix : 106.187.0.0/18 AS Name : KDDI country : Japan ISP Info : LINODE LLC inetnum: 106.187.40.0 - 106.187.47.255 netname: LINODE descr: Linode, LLC country: JP admin-c: KB2156JP tech-c: KB2156JP remarks: This information has been partially mirrored by APNIC from remarks: JPNIC. To obtain more specific information, please use the remarks: JPNIC WHOIS Gateway at remarks: http://www.nic.ad.jp/en/db/whois/en-gateway.html or remarks: whois.nic.ad.jp for WHOIS client. (The WHOIS client remarks: defaults to Japanese output, use the /e switch for English remarks: output) changed: apnic-ftp@nic.ad.jp 20110714 changed: apnic-ftp@nic.ad.jp 20110811 source: JPNIC Contact Information: [担当者情報] a. [JPNICハンドル] KB2156JP b. [氏名] Brett Kaplan c. [Last, First] Brett, Kaplan d. [電子メイル] bKaplan@linode.com f. [組織名] Linode, LLC g. [Organization] Linode, LLC k. [部署] l. [Division] m. [肩書] n. [Title] o. [電話番号] +1-609-593-7103 p. [FAX番号] y. [通知アドレス] [最終更新] 2011/07/14 14:20:07(JST) db-staff@nic.ad.jp IPトレースに付いての場所(IP-GEOLOCATOR)
感染されたのサイト/マルウェアが発見さえたサイトのDNSのDUMP!情報↓ 全てレコードを出しましょう!↓ diybbb.com. 476 IN A 106.187.46.93 www.diybbb.com. 454 IN A 106.187.46.93 diybbb.com. 476 IN SOA f1g1ns1.dnspod.net. freednsadmin.dnspod.com. 1324728081 3600 180 1209600 180 diybbb.com. 476 IN TXT "v=spf1 include:spf.163.com ~all" spf.163.com. 17921 IN TXT "v=spf1 include:a.spf.163.com include:b.spf.163.com -all" a.spf.163.com. 18000 IN TXT "v=spf1 ip4:220.181.12.0/22 ip4:220.181.31.0/24 ip4:123.125.50.0/24 ip4:220.181.72.0/24 ip4:123.58.178.0/24 ip4:123.58.177.0/24 ip4:42.99.128.0/28 ip4:113.108.225.0/24 ip4:218.107.63.0/24 -all" b.spf.163.com. 18000 IN TXT "v=spf1 ip4:176.32.85.45 ip4:176.32.86.149 ip4:46.51.243.229 ip4:176.34.24.103 ip4:176.34.24.136 ip4:176.34.26.118 -all" diybbb.com. 476 IN MX 10 mx.ym.163.com. diybbb.com. 476 IN NS f1g1ns2.dnspod.net. diybbb.com. 476 IN NS f1g1ns1.dnspod.net. diybbb.com. 476 IN NS f1g1ns1.dnspod.net. diybbb.com. 476 IN NS f1g1ns2.dnspod.net. f1g1ns1.dnspod.net. 164000 IN A 119.167.195.6 f1g1ns1.dnspod.net. 164000 IN A 122.225.217.192 f1g1ns1.dnspod.net. 164000 IN A 180.153.10.150 f1g1ns1.dnspod.net. 164000 IN A 183.60.52.217 f1g1ns2.dnspod.net. 164977 IN A 112.90.143.29 f1g1ns2.dnspod.net. 164977 IN A 122.225.217.191 f1g1ns2.dnspod.net. 164977 IN A 180.153.10.151 f1g1ns2.dnspod.net. 164977 IN A 180.153.162.150 +-f1g1ns1.dnspod.net (119.167.195.6) | +-f1g1ns1.dnspod.net (122.225.217.192) | | +-f1g1ns1.dnspod.net (180.153.10.150) | | | +-f1g1ns1.dnspod.net (183.60.52.217) | | | | +-f1g1ns2.dnspod.net (122.225.217.191) | | | | | +-f1g1ns2.dnspod.net (180.153.10.151) | | | | | | +-f1g1ns2.dnspod.net (180.153.162.150) | | | | | | | +-f1g1ns2.dnspod.net (112.90.143.29) | | | | | | | | --------------------------------------------------------------------------------------- Tracing to diybbb.com[a] via 202.238.95.24, maximum of 1 retries 202.238.95.24 (202.238.95.24) --------------------------------------------------------------------------------------- |\___ c.gtld-servers.net [com] (192.26.92.30) | |\___ f1g1ns2.dnspod.net [diybbb.com] (180.153.162.150) Got authoritative answer | |\___ f1g1ns2.dnspod.net [diybbb.com] (180.153.10.151) Got authoritative answer | |\___ f1g1ns2.dnspod.net [diybbb.com] (122.225.217.191) Got authoritative answer | |\___ f1g1ns2.dnspod.net [diybbb.com] (112.90.143.29) Got authoritative answer | |\___ f1g1ns1.dnspod.net [diybbb.com] (183.60.52.217) * | |\___ f1g1ns1.dnspod.net [diybbb.com] (180.153.10.150) * | |\___ f1g1ns1.dnspod.net [diybbb.com] (122.225.217.192) Got authoritative answer | \___ f1g1ns1.dnspod.net [diybbb.com] (119.167.195.6) * |\___ b.gtld-servers.net [com] (2001:0503:231d:0000:0000:0000:0002:0030) * |\___ b.gtld-servers.net [com] (192.33.14.30) | |\___ f1g1ns2.dnspod.net [diybbb.com] (180.153.162.150) Got authoritative answer | |\___ f1g1ns2.dnspod.net [diybbb.com] (180.153.10.151) * | |\___ f1g1ns2.dnspod.net [diybbb.com] (122.225.217.191) Got authoritative answer | |\___ f1g1ns2.dnspod.net [diybbb.com] (112.90.143.29) Got authoritative answer | |\___ f1g1ns1.dnspod.net [diybbb.com] (183.60.52.217) Got authoritative answer [received type is cname] | |\___ f1g1ns1.dnspod.net [diybbb.com] (180.153.10.150) Got authoritative answer | |\___ f1g1ns1.dnspod.net [diybbb.com] (122.225.217.192) Got authoritative answer | \___ f1g1ns1.dnspod.net [diybbb.com] (119.167.195.6) * |\___ e.gtld-servers.net [com] (192.12.94.30) | |\___ f1g1ns2.dnspod.net [diybbb.com] (180.153.162.150) Got authoritative answer | |\___ f1g1ns2.dnspod.net [diybbb.com] (180.153.10.151) Got authoritative answer | |\___ f1g1ns2.dnspod.net [diybbb.com] (122.225.217.191) Got authoritative answer | |\___ f1g1ns2.dnspod.net [diybbb.com] (112.90.143.29) Got authoritative answer | |\___ f1g1ns1.dnspod.net [diybbb.com] (183.60.52.217) Got authoritative answer [received type is cname] | |\___ f1g1ns1.dnspod.net [diybbb.com] (180.153.10.150) Got authoritative answer | |\___ f1g1ns1.dnspod.net [diybbb.com] (122.225.217.192) Got authoritative answer | \___ f1g1ns1.dnspod.net [diybbb.com] (119.167.195.6) * |\___ f.gtld-servers.net [com] (192.35.51.30) | |\___ f1g1ns2.dnspod.net [diybbb.com] (180.153.162.150) * | |\___ f1g1ns2.dnspod.net [diybbb.com] (180.153.10.151) * | |\___ f1g1ns2.dnspod.net [diybbb.com] (122.225.217.191) Got authoritative answer | |\___ f1g1ns2.dnspod.net [diybbb.com] (112.90.143.29) Got authoritative answer | |\___ f1g1ns1.dnspod.net [diybbb.com] (183.60.52.217) Got authoritative answer [received type is cname] | |\___ f1g1ns1.dnspod.net [diybbb.com] (180.153.10.150) Got authoritative answer | |\___ f1g1ns1.dnspod.net [diybbb.com] (122.225.217.192) Got authoritative answer | \___ f1g1ns1.dnspod.net [diybbb.com] (119.167.195.6) * |\___ k.gtld-servers.net [com] (192.52.178.30) | |\___ f1g1ns2.dnspod.net [diybbb.com] (180.153.162.150) Got authoritative answer | |\___ f1g1ns2.dnspod.net [diybbb.com] (180.153.10.151) Got authoritative answer | |\___ f1g1ns2.dnspod.net [diybbb.com] (122.225.217.191) Got authoritative answer | |\___ f1g1ns2.dnspod.net [diybbb.com] (112.90.143.29) Got authoritative answer | |\___ f1g1ns1.dnspod.net [diybbb.com] (183.60.52.217) Got authoritative answer [received type is cname] | |\___ f1g1ns1.dnspod.net [diybbb.com] (180.153.10.150) Got authoritative answer | |\___ f1g1ns1.dnspod.net [diybbb.com] (122.225.217.192) Got authoritative answer | \___ f1g1ns1.dnspod.net [diybbb.com] (119.167.195.6) * |\___ g.gtld-servers.net [com] (192.42.93.30) | |\___ f1g1ns2.dnspod.net [diybbb.com] (180.153.162.150) Got authoritative answer | |\___ f1g1ns2.dnspod.net [diybbb.com] (180.153.10.151) Got authoritative answer | |\___ f1g1ns2.dnspod.net [diybbb.com] (122.225.217.191) Got authoritative answer | |\___ f1g1ns2.dnspod.net [diybbb.com] (112.90.143.29) Got authoritative answer | |\___ f1g1ns1.dnspod.net [diybbb.com] (183.60.52.217) Got authoritative answer [received type is cname] | |\___ f1g1ns1.dnspod.net [diybbb.com] (180.153.10.150) Got authoritative answer | |\___ f1g1ns1.dnspod.net [diybbb.com] (122.225.217.192) Got authoritative answer | \___ f1g1ns1.dnspod.net [diybbb.com] (119.167.195.6) * |\___ i.gtld-servers.net [com] (192.43.172.30) | |\___ f1g1ns2.dnspod.net [diybbb.com] (180.153.162.150) Got authoritative answer | |\___ f1g1ns2.dnspod.net [diybbb.com] (180.153.10.151) * | |\___ f1g1ns2.dnspod.net [diybbb.com] (122.225.217.191) Got authoritative answer | |\___ f1g1ns2.dnspod.net [diybbb.com] (112.90.143.29) Got authoritative answer | |\___ f1g1ns1.dnspod.net [diybbb.com] (183.60.52.217) Got authoritative answer [received type is cname] | |\___ f1g1ns1.dnspod.net [diybbb.com] (180.153.10.150) * | |\___ f1g1ns1.dnspod.net [diybbb.com] (122.225.217.192) Got authoritative answer | \___ f1g1ns1.dnspod.net [diybbb.com] (119.167.195.6) * |\___ h.gtld-servers.net [com] (192.54.112.30) | |\___ f1g1ns2.dnspod.net [diybbb.com] (180.153.162.150) * | |\___ f1g1ns2.dnspod.net [diybbb.com] (180.153.10.151) Got authoritative answer | |\___ f1g1ns2.dnspod.net [diybbb.com] (122.225.217.191) Got authoritative answer | |\___ f1g1ns2.dnspod.net [diybbb.com] (112.90.143.29) Got authoritative answer | |\___ f1g1ns1.dnspod.net [diybbb.com] (183.60.52.217) Got authoritative answer [received type is cname] | |\___ f1g1ns1.dnspod.net [diybbb.com] (180.153.10.150) Got authoritative answer | |\___ f1g1ns1.dnspod.net [diybbb.com] (122.225.217.192) Got authoritative answer | \___ f1g1ns1.dnspod.net [diybbb.com] (119.167.195.6) * |\___ m.gtld-servers.net [com] (192.55.83.30) | |\___ f1g1ns2.dnspod.net [diybbb.com] (180.153.162.150) Got authoritative answer | |\___ f1g1ns2.dnspod.net [diybbb.com] (180.153.10.151) * | |\___ f1g1ns2.dnspod.net [diybbb.com] (122.225.217.191) Got authoritative answer | |\___ f1g1ns2.dnspod.net [diybbb.com] (112.90.143.29) Got authoritative answer | |\___ f1g1ns1.dnspod.net [diybbb.com] (183.60.52.217) Got authoritative answer [received type is cname] | |\___ f1g1ns1.dnspod.net [diybbb.com] (180.153.10.150) Got authoritative answer | |\___ f1g1ns1.dnspod.net [diybbb.com] (122.225.217.192) Got authoritative answer | \___ f1g1ns1.dnspod.net [diybbb.com] (119.167.195.6) * |\___ a.gtld-servers.net [com] (2001:0503:a83e:0000:0000:0000:0002:0030) * |\___ a.gtld-servers.net [com] (192.5.6.30) | |\___ f1g1ns2.dnspod.net [diybbb.com] (180.153.162.150) Got authoritative answer | |\___ f1g1ns2.dnspod.net [diybbb.com] (180.153.10.151) Got authoritative answer | |\___ f1g1ns2.dnspod.net [diybbb.com] (122.225.217.191) Got authoritative answer | |\___ f1g1ns2.dnspod.net [diybbb.com] (112.90.143.29) Got authoritative answer | |\___ f1g1ns1.dnspod.net [diybbb.com] (183.60.52.217) Got authoritative answer [cname] | |\___ f1g1ns1.dnspod.net [diybbb.com] (180.153.10.150) * | |\___ f1g1ns1.dnspod.net [diybbb.com] (122.225.217.192) Got authoritative answer | \___ f1g1ns1.dnspod.net [diybbb.com] (119.167.195.6) * |\___ j.gtld-servers.net [com] (192.48.79.30) | |\___ f1g1ns2.dnspod.net [diybbb.com] (180.153.162.150) Got authoritative answer | |\___ f1g1ns2.dnspod.net [diybbb.com] (180.153.10.151) Got authoritative answer | |\___ f1g1ns2.dnspod.net [diybbb.com] (122.225.217.191) Got authoritative answer | |\___ f1g1ns2.dnspod.net [diybbb.com] (112.90.143.29) Got authoritative answer | |\___ f1g1ns1.dnspod.net [diybbb.com] (183.60.52.217) Got authoritative answer [cname] | |\___ f1g1ns1.dnspod.net [diybbb.com] (180.153.10.150) Got authoritative answer | |\___ f1g1ns1.dnspod.net [diybbb.com] (122.225.217.192) Got authoritative answer | \___ f1g1ns1.dnspod.net [diybbb.com] (119.167.195.6) * |\___ l.gtld-servers.net [com] (192.41.162.30) | |\___ f1g1ns2.dnspod.net [diybbb.com] (180.153.162.150) Got authoritative answer | |\___ f1g1ns2.dnspod.net [diybbb.com] (180.153.10.151) Got authoritative answer | |\___ f1g1ns2.dnspod.net [diybbb.com] (122.225.217.191) Got authoritative answer | |\___ f1g1ns2.dnspod.net [diybbb.com] (112.90.143.29) Got authoritative answer | |\___ f1g1ns1.dnspod.net [diybbb.com] (183.60.52.217) Got authoritative answer [cname] | |\___ f1g1ns1.dnspod.net [diybbb.com] (180.153.10.150) Got authoritative answer | |\___ f1g1ns1.dnspod.net [diybbb.com] (122.225.217.192) Got authoritative answer | \___ f1g1ns1.dnspod.net [diybbb.com] (119.167.195.6) * \___ d.gtld-servers.net [com] (192.31.80.30) |\___ f1g1ns2.dnspod.net [diybbb.com] (180.153.162.150) Got authoritative answer |\___ f1g1ns2.dnspod.net [diybbb.com] (180.153.10.151) Got authoritative answer |\___ f1g1ns2.dnspod.net [diybbb.com] (122.225.217.191) Got authoritative answer |\___ f1g1ns2.dnspod.net [diybbb.com] (112.90.143.29) Got authoritative answer |\___ f1g1ns1.dnspod.net [diybbb.com] (183.60.52.217) Got authoritative answer [cname] |\___ f1g1ns1.dnspod.net [diybbb.com] (180.153.10.150) Got authoritative answer |\___ f1g1ns1.dnspod.net [diybbb.com] (122.225.217.192) Got authoritative answer \___ f1g1ns1.dnspod.net [diybbb.com] (119.167.195.6) *
■フォローに付いて
正式に本マルウェア発見情報を報告し、削除の依頼も送りました。行動待ち状況でモニター最中↓
■マルウェアURLのダウンロードが停止
下記のように現在マルウェアダウンロードURLが停止されております。
Mon Jan 30 17:22:09 JST 2012 --17:29:11-- http://diybbb.com/update.exe => `update.exe.2' Resolving diybbb.com... 106.187.46.93 Connecting to diybbb.com|106.187.46.93|:80... << TIME OUT >>
----
ゼロデイ・ジャパン
http://0day.jp
マルウェア研究所
アドリアン・ヘンドリック
Sponsored by: 株式会社ケイエルジェイテック
Tweet
0 件のコメント:
コメントを投稿