--18:51:11--
hxxp://www.trl-y.com/admin/topics/img-s/tmp2/Postal_Amigo_0083・exe
=> `Postal_Amigo_0083.exe'
Resolving www.trl-y.com... 203.183.81.20
Connecting to www.trl-y.com|203.183.81.20|:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 36,864 (36K) [application/octet-stream]
18:51:11 (191.01 KB/s) - `Postal_Amigo_0083.exe' saved [36864/36864]下記のスパイウェアを発見↓MD5: f8130f30f5370d0fa8a5132715c3abfb
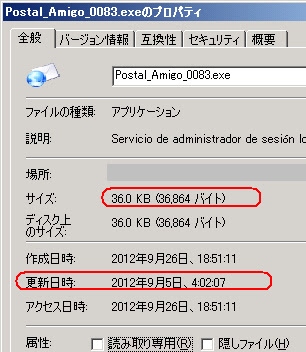
File size: 36.0 KB ( 36864 bytes )
File name: Postal_Amigo_0083.exe
File type: Win32 EXE
Tags: peexe
Detection: 20 / 43
URL: [CLICK]
File size: 36.0 KB ( 36864 bytes )
File name: Postal_Amigo_0083.exe
File type: Win32 EXE
Tags: peexe
Detection: 20 / 43
URL: [CLICK]
マルウェア名前↓
F-Secure : Gen:Trojan.Heur.VP2.cm0@a8K2WgP DrWeb : Trojan.DownLoader6.54403 GData : Gen:Trojan.Heur.VP2.cm0@a8K2WgP VIPRE : Trojan.Win32.Generic!BT Symantec : WS.Reputation.1 Norman : W32/Troj_Generic.ECWYG McAfee-GW-Edition : Artemis!F8130F30F537 TrendMicro-HouseCall : TROJ_GEN.RCBB1IM Avast : Win32:Spyware-gen [Spy] Ikarus : Trojan.Win32.Spy CAT-QuickHeal : (Suspicious) - DNAScan BitDefender : Gen:Trojan.Heur.VP2.cm0@a8K2WgP McAfee : Artemis!F8130F30F537 Rising : Trojan.Bancos!47A6 Kingsoft : Win32.Troj.Undef.(kcloud) AntiVir : TR/Spy.36864.1521 Panda : Suspicious file AVG : SHeur4.APMH Emsisoft : Trojan.Win32.Spy!IK Comodo : UnclassifiedMalware見た目↓
調査サマリー↓
PE Sections:
.text 0x1000 0x544c 24576
.data 0x7000 0xc44 4096
.rsrc 0x8000 0xf80 4096
Compiler:
Microsoft Visual Basic v5.0 - v6.0
Registry:
HKLM\Software\Microsoft\Security Center\UACDisableNotify
HKLM\Software\Microsoft\Windows\CurrentVersion\policies\system\EnableLUA
ファイル保存/変更↓
%System%\wincal.exe ←ずっとプロセスに残っています
%Temp%C:\~DF7831.tmp
%System%\drivers\etc\hosts
ネットワークトラフィック↓
cmawards.com.mx GET /change/change.txt HTTP/1.1
下記のHTTP回答↓
HTTP/1.1 200 OK
Date: Thu, 06 Sep 2012 16:07:12 GMT
Server: Apache/2
Last-Modified: Tue, 04 Sep 2012 07:22:41 GMT
ETag: "73b80ee-44e-4c8db1fa2d240"
Accept-Ranges: bytes
Content-Length: 1102
Vary: Accept-Encoding,User-Agent
Content-Type: text/plain
X-Pad: avoid browser bug【注意】HTTPの回答の中に詐欺銀行サイトの情報を発見、PCのhostの中に書き込まれた↓
手続き責任者↓
inetnum: 203.183.81.0 - 203.183.81.127 netname: JOES-NET descr: Joe's Web Hosting Inc. country: JP admin-c: YM12293JP
0 件のコメント:
コメントを投稿