
1. Background
As per requested by a dear friend I was analyzing False Positive (FP) case of a software package as per mentioned below:
Product Name: Blocklist Manager 2.7.7
Binary File Name: Blocklist_Manager_Install_2.7.7.exe
Maker/Vendor: Bluetack Security Solutions (B.I.S.S.)
Product Official URL: http://blocklistpro.com/the-blocklist-manager-2.7.7.html
Download Source URL: http://www.filecluster.com/downloads/Blocklist-Manager.html
File size : 2150549 bytes
MD5 : eb26ebec97155a1892c2c228efdcdbc0
Icon:

Binary File Name: Blocklist_Manager_Install_2.7.7.exe
Maker/Vendor: Bluetack Security Solutions (B.I.S.S.)
Product Official URL: http://blocklistpro.com/the-blocklist-manager-2.7.7.html
Download Source URL: http://www.filecluster.com/downloads/Blocklist-Manager.html
File size : 2150549 bytes
MD5 : eb26ebec97155a1892c2c228efdcdbc0
Icon:

Some users are using the product as network analysis tools, which is the software is meant to be. However many AntiVirus scanner products are producing alerts related to the product like the following information:
Reference : Virus Total
Date: Sat Jan 7 12:27:09 JST 2012
Hash: f275fae7142a645568e146cc5ffa85b22e9c3d8d26569d011dca104bff2bacb2
URL: http://www.virustotal.com/file-scan/report.html?id=f275fae7142a645568e146cc5ffa85b22e9c3d8d26569d011dca104bff2bacb2-1325906532
Result as per Sat Jan 7 12:27:09 JST 2012
APPL/AngryIPScan
Application.HackTool.AngryIpScanner.B
W32/HackToolX.PK
Application.Win32.BLM.~A
Tool.AngryIpscan.7
Win32.NetTool.Portsc
W32/HackToolX.PK
Application.HackTool.AngryIpScanner
HackerTool/Portscan
Application.HackTool.AngryIpScanner.B
Unwanted-Program
not-a-virus:NetTool.Win32.Portscan.c
Tool:Win32/Angryscan.A
Win32/NetTool.Portscan.C
Spyware.ADH
HKTL_WFPDISABLB
Not_a_virus:NetTool.Portscan.2150549
The definition of the product itself as per mentioned in the vendor's page is as per below:Date: Sat Jan 7 12:27:09 JST 2012
Hash: f275fae7142a645568e146cc5ffa85b22e9c3d8d26569d011dca104bff2bacb2
URL: http://www.virustotal.com/file-scan/report.html?id=f275fae7142a645568e146cc5ffa85b22e9c3d8d26569d011dca104bff2bacb2-1325906532
Result as per Sat Jan 7 12:27:09 JST 2012
APPL/AngryIPScan
Application.HackTool.AngryIpScanner.B
W32/HackToolX.PK
Application.Win32.BLM.~A
Tool.AngryIpscan.7
Win32.NetTool.Portsc
W32/HackToolX.PK
Application.HackTool.AngryIpScanner
HackerTool/Portscan
Application.HackTool.AngryIpScanner.B
Unwanted-Program
not-a-virus:NetTool.Win32.Portscan.c
Tool:Win32/Angryscan.A
Win32/NetTool.Portscan.C
Spyware.ADH
HKTL_WFPDISABLB
Not_a_virus:NetTool.Portscan.2150549
The Blocklist Manager (BLM) is an all-in-one network security tool, allowing you to download a number of regularly updated IP blocklists maintained by BISSLabs.
The above explanation is a straight forward sentence explaining the product and its functionality. The vendor itself aware of the False Positive(FP) caused by some AntiVirus scanner and mentioned in its page the statement below:
As per stated above, The Blocklist Manager 2.7.7 ships with an addon called the Angry IP Scanner which causing some FP's.
2. Goal & Challenge
Regarding to the above background, I would like to investigate the below challenge list by my poor blog writting, with the goal to improve Software maker knowhow in developing software with avoiding FP and AntiVirus products to prevent such False Positive occur in the future. This report will be useful to you if you came into analyzing a false positive case.
1. Is there really any malware attached in the software's installer file (Blocklist_Manager_Install_2.7.7.exe) ? If not, what caused the False Positive/FP of the installation file?
2. Why Angry IP Scanner addon causing many FP? How Angry IP Scanner got installed?
3. Can either Blocklist Manager 2.7.7 or Angry IP Scanner be categorized as malicious software/malware?
2. Why Angry IP Scanner addon causing many FP? How Angry IP Scanner got installed?
3. Can either Blocklist Manager 2.7.7 or Angry IP Scanner be categorized as malicious software/malware?
3. Proof of Concept (binary analysis)
For the start let's analyze the installer Blocklist_Manager_Install_2.7.7.exe binary itself, I manually trace it and found the following details for this binary, I put my comment in the bracket:
3.1. Valid PE file (Valid binary, microsoft windows executional file)
3.2. Mentioned CRC and Actual CRC are different: Mentioned: 0, Actual: 2,179,098 (this may trigger some suspicious alert in many auto scanning)
3.3. File timestamp shows 0x2A425E19 [Fri Jun 19 22:22:17 1992 UTC] (kind of suspicious for the 2007th released software, this may trigger some suspicious alert in many auto scanning)
3.4. Compile Time shows 1992-06-20 07:22:17 (kind of suspicious for the 2007th released software, this may trigger some suspicious alert in many auto scanning)
3.5. In was compiled with packer Inno Setup Module v5 which doesn't exist in 1992(this may trigger some suspicious alert in many auto scanning)
3.6. It triggered some suspicious entropi in some image section headers (saw this many times & packer based installer always shows this sign)
3.7. DLL's Trace Calls Analysis
Which tracing the DLL handles for the installer binary, I found the 3 things which will trigger important alert, let me describe as per below:
3.8. The Pattern Matching Theory
Using some tools I get a random signature binary of the current sample with the value of ep_only = false & section_start_only = true to analyze the FP for the pattern database matching for antivirus product, this methodology is an old school based to check wether some AV having the FP scan result of the analyzed binary as the result of the pattern matching, and below is the details:
I saved each binary into by binary editor:
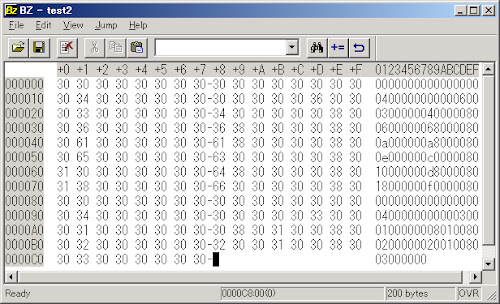
thus separate them and runs VT scanner on them one by one, as plain as that, all shows the result of undetected

I did it more like 30 times with the random signatures, and all saying same stuffs.. No match. Which all of this says that I think no AV vendors is scanning the installer and judging with the simple binary pattern matching method only. The FP result must triggered by the suspicious code in installation binary.
3.9. The Version Info
In this part the vendor is putting the official data of this product which is legitimate info, as per below:
3.2. Mentioned CRC and Actual CRC are different: Mentioned: 0, Actual: 2,179,098 (this may trigger some suspicious alert in many auto scanning)
3.3. File timestamp shows 0x2A425E19 [Fri Jun 19 22:22:17 1992 UTC] (kind of suspicious for the 2007th released software, this may trigger some suspicious alert in many auto scanning)
3.4. Compile Time shows 1992-06-20 07:22:17 (kind of suspicious for the 2007th released software, this may trigger some suspicious alert in many auto scanning)
3.5. In was compiled with packer Inno Setup Module v5 which doesn't exist in 1992(this may trigger some suspicious alert in many auto scanning)
3.6. It triggered some suspicious entropi in some image section headers (saw this many times & packer based installer always shows this sign)
3.6.1. Entropy 0.0 [IMAGE_SECTION_HEADER] Name: BSS Misc: 0xE34 Misc_PhysicalAddress: 0xE34 Misc_VirtualSize: 0xE34 VirtualAddress: 0xB000 SizeOfRawData: 0x0 PointerToRawData: 0x9800 PointerToRelocations: 0x0 PointerToLinenumbers: 0x0 NumberOfRelocations: 0x0 NumberOfLinenumbers: 0x0 Characteristics: 0xC0000000 3.6.2. Entropy 0.0 [IMAGE_SECTION_HEADER] Name: .tls Misc: 0x8 Misc_PhysicalAddress: 0x8 Misc_VirtualSize: 0x8 VirtualAddress: 0xD000 SizeOfRawData: 0x0 PointerToRawData: 0xA200 PointerToRelocations: 0x0 PointerToLinenumbers: 0x0 NumberOfRelocations: 0x0 NumberOfLinenumbers: 0x0 Characteristics: 0xC0000000 3.6.3. Entropy 0.199107517787 [IMAGE_SECTION_HEADER] Name: .rdata Misc: 0x18 Misc_PhysicalAddress: 0x18 Misc_VirtualSize: 0x18 VirtualAddress: 0xE000 SizeOfRawData: 0x200 PointerToRawData: 0xA200 PointerToRelocations: 0x0 PointerToLinenumbers: 0x0 NumberOfRelocations: 0x0 NumberOfLinenumbers: 0x0 Characteristics: 0x50000040 3.6.4. Entropy 0.0 [IMAGE_SECTION_HEADER] Name: .reloc Misc: 0x8A0 Misc_PhysicalAddress: 0x8A0 Misc_VirtualSize: 0x8A0 VirtualAddress: 0xF000 SizeOfRawData: 0x0 PointerToRawData: 0xA400 PointerToRelocations: 0x0 PointerToLinenumbers: 0x0 NumberOfRelocations: 0x0 NumberOfLinenumbers: 0x0 Characteristics: 0x50000040
3.7. DLL's Trace Calls Analysis
Which tracing the DLL handles for the installer binary, I found the 3 things which will trigger important alert, let me describe as per below:
3.7.1. Anti Debugging Traces
3.7.2. File System Activity Traces
3.7.3. DEP Setting Change Trace Calls:
In my opinion the vendor should not go this far to make any installation works. Maybe (again, MAYBE) the vendor sees many FP for this installer, in order to override FP detected in the Windows Malware Protection or Anti Viral Software (whatever it is) he implemented this calls.
3.7.4. Privilege Escalation trace found!
DesiredAccess [in] specifies an access mask that specifies the requested types of access to the access token. These requested access types are compared with the discretionary access control list (DACL) of the token to determine which accesses are granted or denied.
And TokenHandle [out] is pointer contains value to a handle that identifies the newly opened access token when the function returns.
ref: MSDN http://msdn.microsoft.com/en-us/library/windows/desktop/aa379295%28v=vs.85%29.aspx
In the simple english: It means the installer is attempting to access other system's other process for some purpose. If the accessed process will be the other user's foreign process this will be a possible Privilage Escalation attempt. Many memory injection malwares are using this method in order to inject itself to a running process in the memory. So this is also causing a huge alert in some antivirus product while scanning this binary/installer.
3.7.5. TLS aware Trace Calls:
*)Additionally these are the [IMAGE_TLS_DIRECTORY] values:
0x40c120 CloseHandle 0x40c19c LoadLibraryA 0x40c1b8 GetProcAddress 0x40c1e0 GetCurrentProcess 0x40c208 CloseHandleEx: Many Anti Debugging software/systems using the similar trace as per listed above, some are goodware packer based installer and some are security/hacking tools, the rest are malwares, cannot tell only by this trace info.
3.7.2. File System Activity Traces
0x40c11c CreateFileA 0x40c1d4 GetFileAttributesA 0x40c1fc CreateProcessA 0x40c200 CreateFileAEx: Call Traces details as per above often detected in malicious software due to its attempt to infect/exploit the victim, yet, often I saw some software installer tools are using the same method, specially the homebrew ones. There is a de facto in the developer to making the installer to avoid the above tracing calls.
3.7.3. DEP Setting Change Trace Calls:
0x40c0c8 VirtualAlloc 0x40c168 VirtualProtect 0x40c170 VirtualAllocEx: This is a definitely against the security policy for changing the DEP setting in the Windows setting by the user. However, few developer actually does it in order to make sure the installation will go as per expected.
In my opinion the vendor should not go this far to make any installation works. Maybe (again, MAYBE) the vendor sees many FP for this installer, in order to override FP detected in the Windows Malware Protection or Anti Viral Software (whatever it is) he implemented this calls.
3.7.4. Privilege Escalation trace found!
0x40c154 OpenProcessTokenEx: Let me explain the above calls. OpenProcessToken function opens the access token associated with a process with the below syntax:
BOOL WINAPI OpenProcessToken( __in HANDLE ProcessHandle, __in DWORD DesiredAccess, __out PHANDLE TokenHandle );ProcessHandle [in] is a handle to the process whose access token is opened. The process must have the PROCESS_QUERY_INFORMATION access permission.
DesiredAccess [in] specifies an access mask that specifies the requested types of access to the access token. These requested access types are compared with the discretionary access control list (DACL) of the token to determine which accesses are granted or denied.
And TokenHandle [out] is pointer contains value to a handle that identifies the newly opened access token when the function returns.
ref: MSDN http://msdn.microsoft.com/en-us/library/windows/desktop/aa379295%28v=vs.85%29.aspx
In the simple english: It means the installer is attempting to access other system's other process for some purpose. If the accessed process will be the other user's foreign process this will be a possible Privilage Escalation attempt. Many memory injection malwares are using this method in order to inject itself to a running process in the memory. So this is also causing a huge alert in some antivirus product while scanning this binary/installer.
3.7.5. TLS aware Trace Calls:
0x40c0d8 TlsSetValue 0x40c0dc TlsGetValueEx: TlsGetValue is exported by kernel32.dll. Retrieves the value in the calling thread's thread local storage (TLS) slot for the specified TLS index. Each thread of a process has its own slot for each TLS index. I don't know why the maker is accessing this calls. Unfortunately this function often used by the FakeAV installer as per listed here. This will trigger the scan alert too.
*)Additionally these are the [IMAGE_TLS_DIRECTORY] values:
StartAddressOfRawData: 0x40D000 EndAddressOfRawData: 0x40D008 AddressOfIndex: 0x40B3D0 AddressOfCallBacks: 0x40E010 SizeOfZeroFill: 0x0 Characteristics: 0x0
3.8. The Pattern Matching Theory
Using some tools I get a random signature binary of the current sample with the value of ep_only = false & section_start_only = true to analyze the FP for the pattern database matching for antivirus product, this methodology is an old school based to check wether some AV having the FP scan result of the analyzed binary as the result of the pattern matching, and below is the details:
[Section(1/8,CODE)] signature = 0a 06 73 74 72 69 6e 67 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 3c 10 40 00 00 00 00 00 6d 11 40 00 04 00 00 00 00 00 00 00 c4 29 40 00 ac 28 40 00 d4 28 40 00 18 29 40 00 11 00 0b 00 24 29 40 00 04 46 72 65 65 13 00 30 29 40 00 0c 49 6e 69 74 49 6e 73 74 61 6e 63 65 16 00 4c 29 40 00 0f 43 [Section(2/8,DATA)] signature = 00 8d 40 00 d4 1f 40 00 5c 21 40 00 d0 24 40 00 32 13 8b c0 52 75 6e 74 69 6d 65 20 65 72 72 6f 72 20 20 20 20 20 61 74 20 30 30 30 30 30 30 30 30 00 45 72 72 6f 72 00 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 [Section(4/8,.idata)] signature = 00 00 00 00 00 00 00 00 00 00 00 00 54 c2 00 00 b4 c0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 3a c4 00 00 28 c1 00 00 00 00 00 00 00 00 00 00 00 00 00 00 54 c4 00 00 30 c1 00 00 00 00 00 00 00 00 00 00 00 00 00 00 be c4 00 00 48 c1 00 00 00 00 00 00 00 00 00 00 00 00 00 00 2a c5 00 00 60 c1 00 00 [Section(6/8,.rdata)] signature = 00 d0 40 00 08 d0 40 00 d0 b3 40 00 10 e0 40 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 [Section(8/8,.rsrc)] signature = 00 00 00 00 00 00 00 00 04 00 00 00 00 00 06 00 03 00 00 00 40 00 00 80 06 00 00 00 68 00 00 80 0a 00 00 00 a8 00 00 80 0e 00 00 00 c0 00 00 80 10 00 00 00 d8 00 00 80 18 00 00 00 f0 00 00 80 00 00 00 00 00 00 00 00 04 00 00 00 00 00 03 00 01 00 00 00 08 01 00 80 02 00 00 00 20 01 00 80 03 00 00 00
I saved each binary into by binary editor:

thus separate them and runs VT scanner on them one by one, as plain as that, all shows the result of undetected

I did it more like 30 times with the random signatures, and all saying same stuffs.. No match. Which all of this says that I think no AV vendors is scanning the installer and judging with the simple binary pattern matching method only. The FP result must triggered by the suspicious code in installation binary.
3.9. The Version Info
In this part the vendor is putting the official data of this product which is legitimate info, as per below:
LegalCopyright: Copyright\xa9 2005-2007,B.I.S.S. FileDescription: IP List Managemement Tool FileVersion: 2.7.7 Comments: This installation was built with Inno Setup. CompanyName: B.I.S.S.
4. Proof of Concept (Behavior Analysis)
I am not going to judging anything here, the above binary analysis result cannot tell much unless we run and test the samle itself. I just want to see how the product is working, so I just run it in my RAT. And below is the screenshot as evidence and some pointers.
4.2. A suspicious object in the file list is:
%ProgramFiles%\Bluetack\Blocklist Manager\Tools\ipscan.exe (which is the Angry IP Scanner tool) size: 111,104 bytesWith the following details: Product Name: Angry IP scanner 2.21
Binary File Name: ipscan.exe
Maker/Vendor: The program is written and maintained by Anton Keks
Product Official URL: http://www.angryip.org/w/Home and http://sourceforge.net/projects/ipscan/
File size : 111,104 bytes
MD5 : 6c1bcf0b1297689c8c4c12cc70996a75
Icon:

Binary File Name: ipscan.exe
Maker/Vendor: The program is written and maintained by Anton Keks
Product Official URL: http://www.angryip.org/w/Home and http://sourceforge.net/projects/ipscan/
File size : 111,104 bytes
MD5 : 6c1bcf0b1297689c8c4c12cc70996a75
Icon:

4.3. How the installation goes? How the Angry IP Scanner got installed?
The installation goes smoothly well, so does the uninstall procedure. Below are the pics I took from my RAT during running and tests it, during the installation it was announced the additional tools to be installed, and among them the user is having the option to choose the tools to install too.
Installation binary executed:

Installer starts..

Announcement of what will be installed.. you can see the full text here.

Select the component to install..

Installation directory snapshot..

Blocklist Manager products upon execution..

Under the .\Tools directory of the base installation file there is the Angry IP Scanner (ipscan.exe) software which can be executed from the binary call from Blocklist Manager software or directly executing the binary. The snapshot looks like this:

I was using it to scan some of my network, it shows good result like this:

And the system process shows like below during the scanning..
Above looks OK to me. I also run the checking on memory and ports over and over I did not see any malicious act of the software except the port scanning commands provided by this tool. No memory leaks, no nasty stuffs, no infection.
The tools directory itself contains the data as per below:

*) If you take a close look to the date of each programs abive, it shows the different dates, this is might be caused by the vendor was collecting many useful tools together in one packages to ship in the Blocklist Manager 2.7.7
Furthermore, the uninstall process also runs well as per expected...(sorry, sue to limitation of the storage I cannot snapshot every pic..)
4.4. What's wrong behind the installation?
This is the important part, during the installation as per described above, the list of the file was copied to the installation directory, BUT the installer is not only doing that, I detected the below operation of the installer which is triggering alert in some AV scanning software. It is not allowed to change/modify/delete system files for any installation of the 3rf party software:
Following files were deleted:
%System%\MSCOMCTL.OCX
%System%\MSINET.OCX
%System%\RICHTX32.OCX
Following file was modified:
%System%\MSCOMCT2.OCX
%System%\MSCOMCTL.OCX
%System%\MSINET.OCX
%System%\RICHTX32.OCX
Following file was modified:
%System%\MSCOMCT2.OCX
4.5. The False Positive of the Angry IP Scanner (ipscan.exe)
Currently if you scan Angry IP Scanner(ipscan.exe), it will show the following result:
Followings are some of factors which causing the above False Positive/FP :Sat Jan 7 17:39:21 JST 2012 APPL/AngryIPScan Application.HackTool.AngryIpScanner.B PUA.NetTool.IPScan W32/PortScan ApplicUnwnt.Win32.PortScan.C0 Tool.AngryIpscan Riskware.NetTool.AngryIP!IK Win32.Banker W32/PortScan HackerTool/Angry Application.HackTool.AngryIpScanner.B not-a-virus.NetTool.AngryIP AdWare/Portscan.b not-a-virus:NetTool.Win32.Portscan.c PortScan-Angry PortScan-Angry Tool:Win32/Angryscan.A Win32/NetTool.Portscan.C SecurityRisk.AngryIPScanner!rem PUP.AngryIPScanner AngryIPScanner Not_a_virus:NetTool.PortScan.111104 *) Ref: VT Hash : 40dc213fe4551740e12cac575a9880753a9dacd510533f31bd7f635e743a7605
4.5.1. Many fake Angry IP Scanner (ipscan.exe) which actually a malware spreadwide in many free download sites. You may check it by Google search.
4.5.2. The below detection points trigger alarm:
The ipscan.exe's binary has differences in CRC check: Claimed CRC & Actual CRC are different (Claimed: 0/Actual: 167,802)
In the binary code of ipscan.exe was detected the AntiDebug calls : 0x44a428 LoadLibraryA & 0x44a42c GetProcAddress
Some security expert sites marked this software as malware like Threat Expert and Webroot Logo Prevx Research Division for some reasons.
Its port scanning functionality of the software raises many alerts during scanning. For example like stated in this site, it raises the following alerts:
* Can communicate with other computers using TCP protocols
* Communicates with other computers using FTP connections
* Can communicate with other computers using TELNET protocols
* Can Send email using SMTP protocols
* Can communicate with other computer systems using HTTP protocols
* Can examine and send Email using POP3 protocols
* Performs DNS look ups to resolve URL IP addresses
* Makes outbound connections to other computers using NETBIOSOUT protocols
*) many BotNet malwares has the similar characteristic
4.5.2. The below detection points trigger alarm:
*) many BotNet malwares has the similar characteristic
5. Conclusion
5.1. In my perception, after investigating the products based on the above analysis facts, I came into conclusion that Blocklist Manager 2.7.7 and its add-on tool Angry IP scanner (ipscan.exe) are not malicious software indeed. It is a package of a freeware handy security tools for Windows OS platform. As analogy...like a knife, a security tool can be a useful one or a dangerous one, it depends on the person who's using it, yet the tool itself is not malicious.
5.2. However by deeply look into the installation process and understanding it's components, we can learn how the False Postive result of some AV scanners came up, which actually can be avoided in the future development (hopefully).
5.3. I dedicated this report to my friend and also to the maker of Blocklist Manager 2.7.7 (which you are doing a good work for developing a such handy security tool), the AV vendors and all readers to understand the FP problem deeper.
5.4.Please do not depend on the automation scanning result since not every raised alarm/alert is caused by malware. Automation scanning's most demerit is the False Positive of a useful software like this case. In the above explanation at the Proof of concept bynary analysis parts is what the automation scanning result will be, actually while I tested it it is not a harmful software at all. I suggest that if you have the environment to test an unknown software, please do it so.
5.2. However by deeply look into the installation process and understanding it's components, we can learn how the False Postive result of some AV scanners came up, which actually can be avoided in the future development (hopefully).
5.3. I dedicated this report to my friend and also to the maker of Blocklist Manager 2.7.7 (which you are doing a good work for developing a such handy security tool), the AV vendors and all readers to understand the FP problem deeper.
5.4.Please do not depend on the automation scanning result since not every raised alarm/alert is caused by malware. Automation scanning's most demerit is the False Positive of a useful software like this case. In the above explanation at the Proof of concept bynary analysis parts is what the automation scanning result will be, actually while I tested it it is not a harmful software at all. I suggest that if you have the environment to test an unknown software, please do it so.
6. References
Below are references used in this report:
Block List Pro site - http://blocklistpro.com
Threat Expert - Analysis of angryip
Angry IP Scanner project official site http://sourceforge.net/projects/ipscan/ and http://www.angryip.org/w/Home
Virus Total Scan result of Blocklist_Manager_Install_2.7.7.exe
Virus Total Scan result of Angry IP Scanner
Prevx (Webroot) analysis on fake Angry IP Scanner
----
ゼロデイ・ジャパン/Zero Day JP http://0day.jp
マルウェア研究所/Malware Researcher
アドリアン・ヘンドリック / Hendrik ADRIAN
Sponsored by: 株式会社ケイエルジェイテック
Tweet

0 件のコメント:
コメントを投稿