
I just discovered a false positive for the following legitimate japanese software's installer UPX package with folowing details:
Software Name: Simulation RPG Construction
Software category: Online Game RPG Developer Program
Maker/Country: Copyright © , 1997-2010 Kei Sakamoto/Japan
Software's URL: http://www.src.jpn.org
Software category: Online Game RPG Developer Program
Maker/Country: Copyright © , 1997-2010 Kei Sakamoto/Japan
Software's URL: http://www.src.jpn.org
Which was detected as malware in the following URL:
SRC: http://inui-src.sakura.ne.jp/install/srcall-2_2_33-110418.exe
MD5 : 990c62b52f9d6dc06bb6acf7ad24e502
SHA1 : 973747b3c900306a5b12a744d9459815dec278f5
SHA256: a218aca1f341c31684684f9c1a91e7810bf616effb677e5f18887dd4c13cecd0
i.e.: at this site:
MX-CLEAN (clean-mx.de)
Date: 11-09-28 13:00:29
Scan: (17.5%) Win32:Malware-gen
MD5 : 990c62b52f9d6dc06bb6acf7ad24e502
SHA1 : 973747b3c900306a5b12a744d9459815dec278f5
SHA256: a218aca1f341c31684684f9c1a91e7810bf616effb677e5f18887dd4c13cecd0
i.e.: at this site:
MX-CLEAN (clean-mx.de)
Date: 11-09-28 13:00:29
Scan: (17.5%) Win32:Malware-gen
The using of the below UPX details for the installation of this program is causing some suspicious alerts during the scanning which making this false positive result occured:
UPX 2.90 [LZMA] -> Markus Oberhumer, Laszlo Molnar (Markus & Laszlo) & John Reiser
UPX -> www.upx.sourceforge.net
UPX -> www.upx.sourceforge.net
And also this RPG Developer Software is using a lot of code which was detecting by some AV Scan engine as VB malwares. You can confirm this by yourself after extracting the UPX and scan the files using multiple antivirus products.
=================================
Proof of Concept:
=================================
1. Online scanning (Virus Total):
Virus Total was reporting the malware detection as per below details:
http://www.virustotal.com/file-scan/report.html?id=a218aca1f341c31684684f9c1a91e7810bf616effb677e5f18887dd4c13cecd0-1317208057
Win32:Malware-gen (Avast)
Worm/VB.BFCC (AVG)
Win32:Malware-gen (GData)
Worm/VB.cim (Jiangmin)
W32/VB.bjo (TheHacker)
Worm.VB!LLtC/cabrDg (VirusBuster)
Suspicious file (Panda)
...which making a lot of people was thinking that the object was malware, and this blog is helping to clarify and stated the object is false positive.
Win32:Malware-gen (Avast)
Worm/VB.BFCC (AVG)
Win32:Malware-gen (GData)
Worm/VB.cim (Jiangmin)
W32/VB.bjo (TheHacker)
Worm.VB!LLtC/cabrDg (VirusBuster)
Suspicious file (Panda)
...which making a lot of people was thinking that the object was malware, and this blog is helping to clarify and stated the object is false positive.
2. Malware Analysis:
(Below are most suspicious alerts occured during scanning the sample)
Suspicious points are:
2.1. Claimed CRC and Actual CRC are different
2.2. 2(two) Suspicious calls (LoadLibraryA & GetProcAddress)
2.3. 2(two) Suspicious entropy found (Entropy 0.0 & Entropy 7.90778053868)
2.4. Online scanned showed malware result /Virtot 7 /43 (16.3%)
reasons: Usage of the packer UPX causing the false positive.
2.1. Claimed CRC and Actual CRC are different
2.2. 2(two) Suspicious calls (LoadLibraryA & GetProcAddress)
2.3. 2(two) Suspicious entropy found (Entropy 0.0 & Entropy 7.90778053868)
2.4. Online scanned showed malware result /Virtot 7 /43 (16.3%)
reasons: Usage of the packer UPX causing the false positive.
You can find the more details here:
[+] Valid PE file.
Checking for Packer Signature....
Identified packer :UPX -> www.upx.sourceforge.net
UPX 0.89.6 - 1.02 / 1.05 - 2.90 -> Markus & Laszlo [Overlay]
UPX 2.90 [LZMA] -> Markus Oberhumer, Laszlo Molnar & John Reiser
[+] Verifying CRC from file
Claimed CRC and Actual CRC are different: Suspicious
Claimed: 0
Actual: 9945142
[+] Image Base : 0x400000
[+] Address Of Entry Point: 0x2a540
[+] Compile Time: 2004-02-08 21:45:18
Malware loads following DLLs....
-----------------------------------
KERNEL32.DLL
ADVAPI32.dll
comdlg32.dll
GDI32.dll
ole32.dll
SHELL32.dll
USER32.dll
WINMM.dll
(etc)(see the next section for the list of the DLL etc..)
-----------------------
..and found some suspicious SystemCalls: Anti Debugging traces ID:
-----------------------
0x42b690 LoadLibraryA <=== used for dialog-box, environment etc..
0x42b694 GetProcAddress <=== used for monitoring the installation
-----------------------
2(two) Entropy Suspicious found:
(The below entropy was detected because of the UPX packer used)
------------------------------------------------
Section Name: IMAGE_SECTION_HEADER Entropy 0.0
[IMAGE_SECTION_HEADER]
Name: UPX0
Misc: 0x1A000
Misc_PhysicalAddress: 0x1A000
Misc_VirtualSize: 0x1A000
VirtualAddress: 0x1000
SizeOfRawData: 0x0
PointerToRawData: 0x400
PointerToRelocations: 0x0
PointerToLinenumbers: 0x0
NumberOfRelocations: 0x0
NumberOfLinenumbers: 0x0
Characteristics: 0xE0000080
Section Name: IMAGE_SECTION_HEADER Entropy 7.90778053868
[IMAGE_SECTION_HEADER]
Name: UPX1
Misc: 0x10000
Misc_PhysicalAddress: 0x10000
Misc_VirtualSize: 0x10000
VirtualAddress: 0x1B000
SizeOfRawData: 0xF800
PointerToRawData: 0x400
PointerToRelocations: 0x0
PointerToLinenumbers: 0x0
NumberOfRelocations: 0x0
NumberOfLinenumbers: 0x0
Characteristics: 0xE0000040
3. Behaviour Analysis (VMware)
Object icon:

Filename: srcall-2_2_33-110418.exe
If executed and showed the installer windows below, it is a Japanese software so the GUI is maybe a bit unreadable for you:
Upon executed I checked the below system processes and found no harms:

(I checked further more to the registry etc, and found nothing significant)

Most of the false positive was triggered by the AdWare. This installer is using a common procedure and no sign of AdWare detected at all:

During installtion tt copies software product data into a specific folder asked during installation:

The process closed well upon installation done and found no strange processes left nor registry changed, tested also after rebooting:
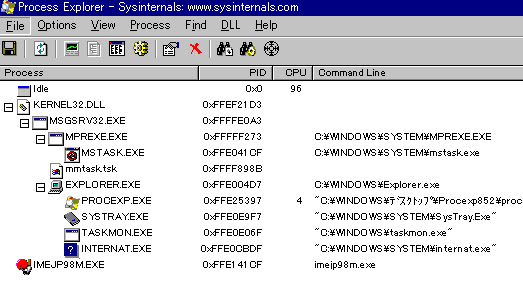
netstat:

These are the files copied into the folder during installation is a data needed to develop an RPG project(as per software is purposed):

These data is using many objects and codes compiled and coded using Microsoft Visual Studio environments, and during operation there are some behaviour checks which can triggered suspicious alerts, also if you scan the files you might be get a false detection too. I checked it and find no harm at all.
If you running it it will goes like this, and ask you to open an game RPG project:

It has official help file which pointed to the software's homepage:
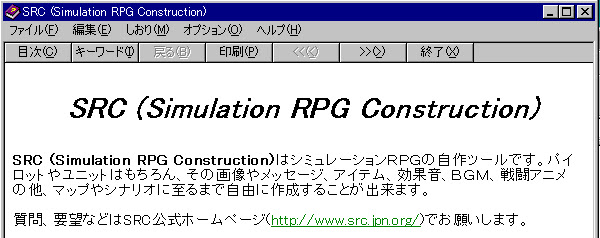
----
ゼロデイ・ジャパン
http://0day.jp
マルウェア研究所
アドリアン・ヘンドリック
Sponsored by: 株式会社ケイエルジェイテック
Tweet
0 件のコメント:
コメントを投稿