URL:hxxp://morllaines.com/file/winsys.exe
本件に付いて下記の不具合点で確実にマルウェアと確認が出来ました↓
1. レジストリーでのIEの設定を変更される動きを発見
2. IEの設定に新しい追加ネットえアーク設定を発見
3. レジストリーでマウスの設定を変更される動きを発見
4. キーボードのシステムコールをフック(モニター)されている状況を発見
5. TCPとUDPバックドアポートを開く動き発見
6. IE個人データを外に送る動きを発見
7. マルウェアのプロセスはずっとメモリーに残ってPCの負荷が上がってしまう動きを発見
8. ウイルストータルのサイトでスキャンしたら結果=[33/40] (82.5%)
2. IEの設定に新しい追加ネットえアーク設定を発見
3. レジストリーでマウスの設定を変更される動きを発見
4. キーボードのシステムコールをフック(モニター)されている状況を発見
5. TCPとUDPバックドアポートを開く動き発見
6. IE個人データを外に送る動きを発見
7. マルウェアのプロセスはずっとメモリーに残ってPCの負荷が上がってしまう動きを発見
8. ウイルストータルのサイトでスキャンしたら結果=[33/40] (82.5%)
簡単な説明は下記となります↓
ダウンロードしたのファイルは下記の形となります↓
ファイルのプロパーティは下記となります↓

このファイルを実行しますとパソコンのCPU負荷が上がってしまいって、winsys.exeプロセスがメモリーの中に発見が出来ます↓
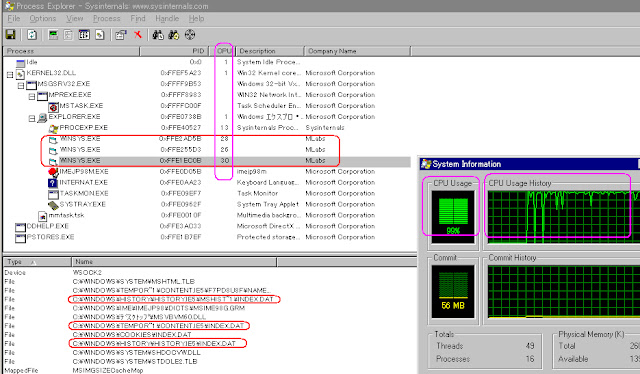
↑IEのファイルがフックされている状況となります(マークされた所)
それでIE関係のスクリプトが実行されてしまうので、IEでのスクリップト機能を無効にしたらポップアップが沢山出てしまいます、そこで繋ぎ先のURL情報が出ました、画像を取りましたので、こんな感じです↓
https://lh3.googleusercontent.com/-WkQTG3bcvQ0/Te9yHbVKDJI/AAAAAAAACNY/x12u17J9lN0/s640/00004.jpg
外にあるリモートサイトに色んな繋ぎが発見、ポップアップのURLドメインにTCP/80の繋ぐ確認が出来ます↓

本件のマルウェアは色んなAVメーカーで検知が出来ましたので、スキャンしたら下記のマルウェア名前となります↓

ファイルのプロパーティは下記となります↓

このファイルを実行しますとパソコンのCPU負荷が上がってしまいって、winsys.exeプロセスがメモリーの中に発見が出来ます↓

↑IEのファイルがフックされている状況となります(マークされた所)
それでIE関係のスクリプトが実行されてしまうので、IEでのスクリップト機能を無効にしたらポップアップが沢山出てしまいます、そこで繋ぎ先のURL情報が出ました、画像を取りましたので、こんな感じです↓
https://lh3.googleusercontent.com/-WkQTG3bcvQ0/Te9yHbVKDJI/AAAAAAAACNY/x12u17J9lN0/s640/00004.jpg
外にあるリモートサイトに色んな繋ぎが発見、ポップアップのURLドメインにTCP/80の繋ぐ確認が出来ます↓

本件のマルウェアは色んなAVメーカーで検知が出来ましたので、スキャンしたら下記のマルウェア名前となります↓
Win-Trojan/Securisk
TR/ATRAPS.Gen
Trojan/Win32.VB.gen
Win32:Malware-gen
Win32:Malware-gen
Clicker.AMOU
Trojan.Generic.5001475
TrojanClicker.VB.fdt
W32/MalwareF.RKSK
UnclassifiedMalware
Trojan-Clicker.Win32.VB!IK
W32/MalwareF.RKSK
Trojan.Generic.5001475
Trojan.Generic.5001475
Trojan-Clicker.Win32.VB
TrojanClicker.VB.czh
Riskware
Trojan-Clicker.Win32.VB.fdt
Generic.dx!tvz
Generic.dx!tvz
Trojan:Win32/Dynamer!dtcDN
W32/Suspicious_Gen2.CTRLS
Trj/StartPage.DAW
Trojan.Gen
Mal/Generic-L
Trojan.Agent/Gen-Koobface[Bonkers]
Trojan.Gen
Trojan/Clicker.VB.fdt
TROJ_GEN.R3EC3IJ
TrojanClicker.VB.fdt
Trojan.Win32.Generic!BT
Trojan.CL.VB!v7PU+tHQjjg
TR/ATRAPS.Gen
Trojan/Win32.VB.gen
Win32:Malware-gen
Win32:Malware-gen
Clicker.AMOU
Trojan.Generic.5001475
TrojanClicker.VB.fdt
W32/MalwareF.RKSK
UnclassifiedMalware
Trojan-Clicker.Win32.VB!IK
W32/MalwareF.RKSK
Trojan.Generic.5001475
Trojan.Generic.5001475
Trojan-Clicker.Win32.VB
TrojanClicker.VB.czh
Riskware
Trojan-Clicker.Win32.VB.fdt
Generic.dx!tvz
Generic.dx!tvz
Trojan:Win32/Dynamer!dtcDN
W32/Suspicious_Gen2.CTRLS
Trj/StartPage.DAW
Trojan.Gen
Mal/Generic-L
Trojan.Agent/Gen-Koobface[Bonkers]
Trojan.Gen
Trojan/Clicker.VB.fdt
TROJ_GEN.R3EC3IJ
TrojanClicker.VB.fdt
Trojan.Win32.Generic!BT
Trojan.CL.VB!v7PU+tHQjjg
ここからマルウェアの研究アナリシス情報を書きます↓
======================================
ファイルの中身調査
======================================
----------------------------------------------------------------------
Filename: winsys.exe
MD5 : 51e5d3455eca0be019795a03978bcdf5
SHA1 : 95f4a4ea8d95b3f15f3874bc14b275392f5bf31d
SHA256: 8a7f67a89e407071837abb944500af4b8d052e3c8a9531140c565b9ff9106d0c
File size : 45,056 bytes
----------------------------------------------------------------------
1. Valid PE file with packer.
2. Identified packer :Microsoft Visual Basic v5.0
3. Loading DLLs:
[+]ole32.dll
[+]oleaut32.dll
[+]kernel32.dll
[+]MSVBVM60.DLL
4. First block Disasemblling:
[0x4010d8L] call 0x4010d2L
[0x4010ddL] add [ax] al
[0x4010e2L] add [ax] al
[0x4010e4L] add [ax] al
[0x4010e6L] xor [ax] al
[0x4010e8L] add [ax] al
[0x4010eaL] inc eax
[0x4010ecL] add [ax] al
[0x4010edL] add [ax] al
[0x4010efL] add [ax] al
[0x4010f1L] add [ax-0x46] bh
[0x4010f3L] enter 0xc4be 0xf1
[0x4010f6L] jecxz 0x401140L
[0x4010faL] mov al [0xab3ab7dfL]
[0x4010fcL] iretd
5. Suspicious section found.
[+]Section Name: IMAGE_SECTION_HEADER Entropy 0.0
[IMAGE_SECTION_HEADER]
Name: .data
Misc: 0x2CE8
Misc_PhysicalAddress: 0x2CE8
Misc_VirtualSize: 0x2CE8
VirtualAddress: 0xA000
SizeOfRawData: 0x0
PointerToRawData: 0x0
PointerToRelocations: 0x0
PointerToLinenumbers: 0x0
NumberOfRelocations: 0x0
NumberOfLinenumbers: 0x0
Characteristics: 0xC0000040
6. Virus Total scan result: Malware detected! [33/40] (82.5%)
[+]Checksum of malware :51e5d3455eca0be019795a03978bcdf5
[+]Malware detected! [33/40] (82.5%)
[+]Scan Reference: http://www.virustotal.com/file-scan/report.html?id=8a7f67a89e407071837abb944500af4b8d052e3c8a9531140c565b9ff9106d0c-1303793682
[+]Malware names:
Win-Trojan/Securisk
TR/ATRAPS.Gen
Trojan/Win32.VB.gen
Win32:Malware-gen
Win32:Malware-gen
Clicker.AMOU
Trojan.Generic.5001475
TrojanClicker.VB.fdt
W32/MalwareF.RKSK
UnclassifiedMalware
Trojan-Clicker.Win32.VB!IK
W32/MalwareF.RKSK
Trojan.Generic.5001475
Trojan.Generic.5001475
Trojan-Clicker.Win32.VB
TrojanClicker.VB.czh
Riskware
Trojan-Clicker.Win32.VB.fdt
Generic.dx!tvz
Generic.dx!tvz
Trojan:Win32/Dynamer!dtc
DN
W32/Suspicious_Gen2.CTRLS
Trj/StartPage.DAW
Trojan.Gen
Mal/Generic-L
Trojan.Agent/Gen-Koobface[Bonkers]
Trojan.Gen
Trojan/Clicker.VB.fdt
TROJ_GEN.R3EC3IJ
TrojanClicker.VB.fdt
Trojan.Win32.Generic!BT
Trojan.CL.VB!v7PU+tHQjjg
7. File Analysis:
[+]ExifTool:
file metadata
CharacterSet: Unicode
CodeSize: 36864
CompanyName: MLabs
EntryPoint: 0x10d8
FileFlagsMask: 0x0000
FileOS: Win32
FileSize: 44 kB
FileSubtype: 0
FileType: Win32 EXE
FileVersion: 2.02
FileVersionNumber: 2.2.0.0
ImageVersion: 2.2
InitializedDataSize: 16384
InternalName: y grupoinvisivel
LanguageCode: English (U.S.)
LinkerVersion: 6.0
MIMEType: application/octet-stream
MachineType: Intel 386 or later, and compatibles
OSVersion: 4.0
ObjectFileType: Executable application
OriginalFilename: y grupoinvisivel.exe
PEType: PE32
ProductName: Winsys32
ProductVersion: 2.02
ProductVersionNumber: 2.2.0.0
Subsystem: Windows GUI
SubsystemVersion: 4.0
TimeStamp: 2010:06:18 17:06:27+02:00
UninitializedDataSize: 0
[+]File Header (DUMP)
Machine: 0x14C
NumberOfSections: 0x3
TimeDateStamp: 0x4C1B8B73 [Fri Jun 18 15:06:27 2010 UTC]
PointerToSymbolTable: 0x0
NumberOfSymbols: 0x0
SizeOfOptionalHeader: 0xE0
Characteristics: 0x10F
Flags: IMAGE_FILE_LOCAL_SYMS_STRIPPED, IMAGE_FILE_32BIT_MACHINE, IMAGE_FILE_EXECUTABLE_IMAGE, IMAGE_FILE_LINE_NUMS_STRIPPED, IMAGE_FILE_RELOCS_STRIPPED
[+]Version Information (DUMP)
[VS_VERSIONINFO]
Length: 0x230
ValueLength: 0x34
Type: 0x0
[VS_FIXEDFILEINFO]
Signature: 0xFEEF04BD
StrucVersion: 0x10000
FileVersionMS: 0x20002
FileVersionLS: 0x0
ProductVersionMS: 0x20002
ProductVersionLS: 0x0
FileFlagsMask: 0x0
FileFlags: 0x0
FileOS: 0x4
FileType: 0x1
FileSubtype: 0x0
FileDateMS: 0x0
FileDateLS: 0x0
[VarFileInfo]
Length: 0x44
ValueLength: 0x0
Type: 0x0
[StringFileInfo]
Length: 0x190
ValueLength: 0x0
Type: 0x1
[StringTable]
Length: 0x16C
ValueLength: 0x0
Type: 0x1
LangID: 040904B0
InternalName: y grupoinvisivel
FileVersion: 2.02
CompanyName: MLabs
ProductName: Winsys32
ProductVersion: 2.02
OriginalFilename: y grupoinvisivel.exe
======================================
BEHAVIOR/マルウェアの動き調査結果
======================================
1. Process-status at analysis end: alive
Process Name Process Filename Main Module Size
------------------------------------------------------------------------------------
[winsys.exe1] [file and pathname \winsys.exe1] 57,344 bytes
------------------------------------------------------------------------------------
2. Load-time Dlls
Module Name Base Address Size
------------------------------------------------------------------
C:\?WINDOWS\?system32\?ntdll.dll 0x7C900000 0x000AF000
C:\?WINDOWS\?system32\?kernel32.dll 0x7C800000 0x000F6000
C:\?WINDOWS\?system32\?ole32.dll 0x774E0000 0x0013D000
C:\?WINDOWS\?system32\?ADVAPI32.dll 0x77DD0000 0x0009B000
C:\?WINDOWS\?system32\?RPCRT4.dll 0x77E70000 0x00092000
C:\?WINDOWS\?system32\?Secur32.dll 0x77FE0000 0x00011000
C:\?WINDOWS\?system32\?GDI32.dll 0x77F10000 0x00049000
C:\?WINDOWS\?system32\?USER32.dll 0x7E410000 0x00091000
C:\?WINDOWS\?system32\?msvcrt.dll 0x77C10000 0x00058000
C:\?WINDOWS\?system32\?oleaut32.dll 0x77120000 0x0008B000
C:\?WINDOWS\?system32\?MSVBVM60.DLL 0x73420000 0x00153000
------------------------------------------------------------------
3. Run-time Dlls
------------------------------------------------------------------
Module Name Base Address Size
C:\?WINDOWS\?system32\?xpsp2res.dll 0x00FB0000 0x002C5000
C:\?WINDOWS\?system32\?xpsp3res.dll 0x20000000 0x000AA000
C:\?WINDOWS\?system32\?UxTheme.dll 0x5AD70000 0x00038000
C:\?WINDOWS\?system32\?NETAPI32.dll 0x5B860000 0x00055000
C:\?WINDOWS\?system32\?comctl32.dll 0x5D090000 0x0009A000
C:\?WINDOWS\?system32\?hnetcfg.dll 0x662B0000 0x00058000
C:\?WINDOWS\?system32\?shdoclc.dll 0x71800000 0x00088000
C:\?WINDOWS\?system32\?mswsock.dll 0x71A50000 0x0003F000
C:\?WINDOWS\?System32\?wshtcpip.dll 0x71A90000 0x00008000
C:\?WINDOWS\?system32\?WS2HELP.dll 0x71AA0000 0x00008000
C:\?WINDOWS\?system32\?WS2_32.dll 0x71AB0000 0x00017000
C:\?WINDOWS\?system32\?wsock32.dll 0x71AD0000 0x00009000
C:\?WINDOWS\?system32\?msls31.dll 0x746C0000 0x00027000
C:\?WINDOWS\?system32\?msimtf.dll 0x746F0000 0x0002A000
C:\?WINDOWS\?system32\?MSCTF.dll 0x74720000 0x0004C000
C:\?WINDOWS\?system32\?RichEd20.dll 0x74E30000 0x0006D000
C:\?WINDOWS\?system32\?CRYPTUI.dll 0x754D0000 0x00080000
C:\?WINDOWS\?system32\?mlang.dll 0x75CF0000 0x00091000
C:\?WINDOWS\?system32\?IMM32.DLL 0x76390000 0x0001D000
C:\?WINDOWS\?system32\?PSAPI.DLL 0x76BF0000 0x0000B000
C:\?WINDOWS\?system32\?WINTRUST.dll 0x76C30000 0x0002E000
C:\?WINDOWS\?system32\?IMAGEHLP.dll 0x76C90000 0x00028000
C:\?WINDOWS\?system32\?WLDAP32.dll 0x76F60000 0x0002C000
C:\?WINDOWS\?system32\?CLBCATQ.DLL 0x76FD0000 0x0007F000
C:\?WINDOWS\?system32\?COMRes.dll 0x77050000 0x000C5000
C:\?WINDOWS\?system32\?WININET.dll 0x771B0000 0x000AA000
C:\?WINDOWS\?WinSxS\?x86_Microsoft.Windows.Common-Controls_6595b64144ccf1df_6.0.2600.5512_x-ww_35d4ce83\?comctl32.dll 0x773D0000 0x00103000
C:\?WINDOWS\?system32\?SETUPAPI.dll 0x77920000 0x000F3000
C:\?WINDOWS\?system32\?CRYPT32.dll 0x77A80000 0x00095000
C:\?WINDOWS\?system32\?MSASN1.dll 0x77B20000 0x00012000
C:\?WINDOWS\?system32\?appHelp.dll 0x77B40000 0x00022000
C:\?WINDOWS\?system32\?VERSION.dll 0x77C00000 0x00008000
C:\?WINDOWS\?system32\?SHLWAPI.dll 0x77F60000 0x00076000
C:\?WINDOWS\?system32\?SHELL32.dll 0x7C9C0000 0x00817000
C:\?WINDOWS\?system32\?mshtml.dll 0x7DC30000 0x002F2000
C:\?WINDOWS\?system32\?urlmon.dll 0x7E1E0000 0x000A2000
C:\?WINDOWS\?system32\?shdocvw.dll 0x7E290000 0x00171000
C:\?WINDOWS\?system32\?SXS.DLL 0x7E720000 0x000B0000
------------------------------------------------------------------
4. Registry Values Modified:
Key Name New Value
------------------------------------------------------------------
4.1. Changing Setting of the Intrenet Explorer:
HKLM\?Software\?Microsoft\?Windows\?CurrentVersion\?Internet Settings\?Cache\?Paths info Directory C:\?Documents and Settings\?Administrator\?Local Settings\?Temporary Internet Files\?Content.IE5
HKLM\?Software\?Microsoft\?Windows\?CurrentVersion\?Internet Settings\?Cache\?Paths info Paths 4
HKLM\?Software\?Microsoft\?Windows\?CurrentVersion\?Internet Settings\?Cache\?Paths\?Path1 info CacheLimit 40852
HKLM\?Software\?Microsoft\?Windows\?CurrentVersion\?Internet Settings\?Cache\?Paths\?Path1 info CachePath C:\?Documents and Settings\?Administrator\?Local Settings\?Temporary Internet Files\?Content.IE5\?Cache1
HKLM\?Software\?Microsoft\?Windows\?CurrentVersion\?Internet Settings\?Cache\?Paths\?Path2 info CacheLimit 40852
HKLM\?Software\?Microsoft\?Windows\?CurrentVersion\?Internet Settings\?Cache\?Paths\?Path2 info CachePath C:\?Documents and Settings\?Administrator\?Local Settings\?Temporary Internet Files\?Content.IE5\?Cache2
HKLM\?Software\?Microsoft\?Windows\?CurrentVersion\?Internet Settings\?Cache\?Paths\?Path3 info CacheLimit 40852
HKLM\?Software\?Microsoft\?Windows\?CurrentVersion\?Internet Settings\?Cache\?Paths\?Path3 info CachePath C:\?Documents and Settings\?Administrator\?Local Settings\?Temporary Internet Files\?Content.IE5\?Cache3
HKLM\?Software\?Microsoft\?Windows\?CurrentVersion\?Internet Settings\?Cache\?Paths\?Path4 info CacheLimit 40852
HKLM\?Software\?Microsoft\?Windows\?CurrentVersion\?Internet Settings\?Cache\?Paths\?Path4 info CachePath C:\?Documents and Settings\?Administrator\?Local Settings\?Temporary Internet Files\?Content.IE5\?Cache4
4.2. Adding the Intranet Setting of the IE:
HKU\?S-1-5-21-842925246-1425521274-308236825-500\?Software\?Microsoft\?Windows\?CurrentVersion\?Internet Settings\?ZoneMap\? info IntranetName 1
HKU\?S-1-5-21-842925246-1425521274-308236825-500\?Software\?Microsoft\?Windows\?CurrentVersion\?Internet Settings\?ZoneMap\? info ProxyBypass 1
HKU\?S-1-5-21-842925246-1425521274-308236825-500\?Software\?Microsoft\?Windows\?CurrentVersion\?Internet Settings\?ZoneMap\? info UNCAsIntranet 1
4.3. Changing Setting of the Mouse Settings:
HKU\?S-1-5-21-842925246-1425521274-308236825-500\?Software\?Microsoft\?Windows\?CurrentVersion\?Explorer\?MountPoints2\?{a1094da8-30a0-11dd-817b-806d6172696f}\? BaseClass Drive
HKU\?S-1-5-21-842925246-1425521274-308236825-500\?Software\?Microsoft\?Windows\?CurrentVersion\?Explorer\?MountPoints2\?{a1094daa-30a0-11dd-817b-806d6172696f}\? BaseClass Drive
4.4. Changing setting for the Explorer Cache/Cookies & Histories:
HKU\?S-1-5-21-842925246-1425521274-308236825-500\?Software\?Microsoft\?Windows\?CurrentVersion\?Explorer\?Shell Folders Cache C:\?Documents and Settings\?Administrator\?Local Settings\?Temporary Internet Files
HKU\?S-1-5-21-842925246-1425521274-308236825-500\?Software\?Microsoft\?Windows\?CurrentVersion\?Explorer\?Shell Folders Cookies C:\?Documents and Settings\?Administrator\?Cookies
HKU\?S-1-5-21-842925246-1425521274-308236825-500\?Software\?Microsoft\?Windows\?CurrentVersion\?Explorer\?Shell Folders History C:\?Documents and Settings\?Administrator\?Local Settings\?History
5. Keyboard Keys Monitored:
Virtual Key Code Times
----------------------------------
VK_SHIFT (16) 12
VK_CONTROL (17) 12
VK_MENU (18) 12
VK_LSHIFT (160) 12
VK_LCONTROL (162) 12
VK_LMENU (164) 12
----------------------------------
6. Mutex Created:
-----------------------------------------------------------------------------
CTF.Asm.MutexDefaultS-?1-?5-?21-?842925246-?1425521274-?308236825-?500
CTF.Compart.MutexDefaultS-?1-?5-?21-?842925246-?1425521274-?308236825-?500
CTF.LBES.MutexDefaultS-?1-?5-?21-?842925246-?1425521274-?308236825-?500
CTF.Layouts.MutexDefaultS-?1-?5-?21-?842925246-?1425521274-?308236825-?500
CTF.TMD.MutexDefaultS-?1-?5-?21-?842925246-?1425521274-?308236825-?500
CTF.TimListCache.FMPDefaultS-?1-?5-?21-?842925246-?1425521274-?308236825-?500MUTEX.DefaultS-?1-?5-?21-?842925246-?1425521274-?308236825-?500
ZonesCacheCounterMutex
ZonesCounterMutex
ZonesLockedCacheCounterMutex
-----------------------------------------------------------------------------
7. Network Activities:
Opening the following Ports as BACKDOORS:
-------------------------------------------
Port Protocol Process
-------------------------------------------
1053 UDP winsys.exe
1055 TCP winsys.exe
1056 TCP winsys.exe
1057 TCP winsys.exe
: :
-----------------------------------------
======================================
マルウェアのネットワークソースの情報
======================================
サイトのスナップショット↓

----------------------------------------------------------------------
--19:18:59-- hxxp://morllaines.com/file/winsys.exe
=> `winsys.exe'
Resolving morllaines.com... 60.37.97.131
Connecting to morllaines.com|60.37.97.131|:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 45,056 (44K) [application/octet-stream]
100%[====================================>] 45,056 252.00K/s
19:19:00 (251.72 KB/s) - `winsys.exe' saved [45056/45056]
----------------------------------------------------------------------
1. NSLOOKUP:
Name: morllaines.com
Address: 60.37.97.131
2. ASN origin 60.37.97.131 からの出力..
4713 | 60.32.0.0/12 | OCN | JP | OCN.NE.JP | OPEN COMPUTER NETWORK
3. WHOIS:
inetnum: 60.32.0.0 - 60.47.255.255
netname: OCN
descr: NTT Communications Corporation
descr: 1-6 Uchisaiwai-cho 1-chome Chiyoda-ku, Tokyo 100-8019 Japan
country: JP
admin-c: JNIC1-AP
tech-c: JNIC1-AP
status: ALLOCATED PORTABLE
remarks: Email address for spam or abuse complaints : abuse@ocn.ad.jp
mnt-by: MAINT-JPNIC
mnt-lower: MAINT-JPNIC
changed: hm-changed@apnic.net 20040402
changed: ip-apnic@nic.ad.jp 20050401
source: APNIC
role: Japan Network Information Center
address: Kokusai-Kougyou-Kanda Bldg 6F, 2-3-4 Uchi-Kanda
address: Chiyoda-ku, Tokyo 101-0047, Japan
country: JP
phone: +81-3-5297-2311
fax-no: +81-3-5297-2312
e-mail: hostmaster@nic.ad.jp
admin-c: JI13-AP
tech-c: JE53-AP
nic-hdl: JNIC1-AP
mnt-by: MAINT-JPNIC
changed: hm-changed@apnic.net 20041222
changed: hm-changed@apnic.net 20050324
changed: ip-apnic@nic.ad.jp 20051027
source: APNIC
inetnum: 60.37.64.0 - 60.37.127.255
netname: OCN
descr: Open Computer Network
country: JP
admin-c: AY1361JP
tech-c: KK551JP
tech-c: TT10660JP
tech-c: TT15086JP
remarks: This information has been partially mirrored by APNIC from
remarks: JPNIC. To obtain more specific information, please use the
remarks: JPNIC WHOIS Gateway at
remarks: http://www.nic.ad.jp/en/db/whois/en-gateway.html or
remarks: whois.nic.ad.jp for WHOIS client. (The WHOIS client
remarks: defaults to Japanese output, use the /e switch for English
remarks: output)
changed: apnic-ftp@nic.ad.jp 20040521
source: JPNIC

----------------------------------------------------------------------
--19:18:59-- hxxp://morllaines.com/file/winsys.exe
=> `winsys.exe'
Resolving morllaines.com... 60.37.97.131
Connecting to morllaines.com|60.37.97.131|:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 45,056 (44K) [application/octet-stream]
100%[====================================>] 45,056 252.00K/s
19:19:00 (251.72 KB/s) - `winsys.exe' saved [45056/45056]
----------------------------------------------------------------------
1. NSLOOKUP:
Name: morllaines.com
Address: 60.37.97.131
2. ASN origin 60.37.97.131 からの出力..
4713 | 60.32.0.0/12 | OCN | JP | OCN.NE.JP | OPEN COMPUTER NETWORK
3. WHOIS:
inetnum: 60.32.0.0 - 60.47.255.255
netname: OCN
descr: NTT Communications Corporation
descr: 1-6 Uchisaiwai-cho 1-chome Chiyoda-ku, Tokyo 100-8019 Japan
country: JP
admin-c: JNIC1-AP
tech-c: JNIC1-AP
status: ALLOCATED PORTABLE
remarks: Email address for spam or abuse complaints : abuse@ocn.ad.jp
mnt-by: MAINT-JPNIC
mnt-lower: MAINT-JPNIC
changed: hm-changed@apnic.net 20040402
changed: ip-apnic@nic.ad.jp 20050401
source: APNIC
role: Japan Network Information Center
address: Kokusai-Kougyou-Kanda Bldg 6F, 2-3-4 Uchi-Kanda
address: Chiyoda-ku, Tokyo 101-0047, Japan
country: JP
phone: +81-3-5297-2311
fax-no: +81-3-5297-2312
e-mail: hostmaster@nic.ad.jp
admin-c: JI13-AP
tech-c: JE53-AP
nic-hdl: JNIC1-AP
mnt-by: MAINT-JPNIC
changed: hm-changed@apnic.net 20041222
changed: hm-changed@apnic.net 20050324
changed: ip-apnic@nic.ad.jp 20051027
source: APNIC
inetnum: 60.37.64.0 - 60.37.127.255
netname: OCN
descr: Open Computer Network
country: JP
admin-c: AY1361JP
tech-c: KK551JP
tech-c: TT10660JP
tech-c: TT15086JP
remarks: This information has been partially mirrored by APNIC from
remarks: JPNIC. To obtain more specific information, please use the
remarks: JPNIC WHOIS Gateway at
remarks: http://www.nic.ad.jp/en/db/whois/en-gateway.html or
remarks: whois.nic.ad.jp for WHOIS client. (The WHOIS client
remarks: defaults to Japanese output, use the /e switch for English
remarks: output)
changed: apnic-ftp@nic.ad.jp 20040521
source: JPNIC
======================================
REFERENCES
======================================
http://www.virustotal.com/file-scan/report.html?id=8a7f67a89e407071837abb944500af4b8d052e3c8a9531140c565b9ff9106d0c-1307529376
http://www.threatexpert.com/report.aspx?md5=51e5d3455eca0be019795a03978bcdf5
https://www.vicheck.ca/md5query.php?hash=https://www.vicheck.ca/md5query.php?hash=51e5d3455eca0be019795a03978bcdf5
http://camas.comodo.com/cgi-bin/submit?file=8a7f67a89e407071837abb944500af4b8d052e3c8a9531140c565b9ff9106d0c
http://www.threatexpert.com/report.aspx?md5=51e5d3455eca0be019795a03978bcdf5
https://www.vicheck.ca/md5query.php?hash=https://www.vicheck.ca/md5query.php?hash=51e5d3455eca0be019795a03978bcdf5
http://camas.comodo.com/cgi-bin/submit?file=8a7f67a89e407071837abb944500af4b8d052e3c8a9531140c565b9ff9106d0c
----
ゼロデイ・ジャパン
http://0day.jp
マルウェア研究所
アドリアン・ヘンドリック
Sponsored by: 株式会社ケイエルジェイテック
Tweet
0 件のコメント:
コメントを投稿