As the background (in case you did not know it), Stop Malvertising security blog is writing a very good explanation about the origin of this issue, which you can access it from here. Thank you to Kimberly for the good explanation.
Expectedly, as pro and cons situation came up upon it, is needed to clarify about what kind of "thing" that we really deal with in the first place. So herewith I will explain it in the easiest way (so don't worry I will not write "too many" list of system calls this time..) about what is the "WinRar v3.71.exe" file really is, and why so many antivirus detecting this file as malware.
1. "WinRar v3.71.exe" What is this file?
"WinRar v3.71.exe" is the file sample of the current topic. Sample can be downloaded from this URL (password=infected) since the real sample in torrent was detected.
Shortly speaking , "WinRar v3.71.exe" is a simply trigger program of the WinRAR, made by Borland Dephi, which is dropping the WinRAR.exe executable files/binaries/programs set into your temporary folder and execute it instead.
While executing the WinRAR, "WinRar v3.71.exe" will run in the memory as "WinRar v3.71.exe" process, and control the entire operation. If you kill the process then the temporary directory and its contents will be permanently deleted by "WinRar v3.71.exe" just before exit. This program is not only dropping this stuffs but also the internet shortcut go straight to some homepage in south east asia.
The further way to explain is, WHY the maker is making it like this? Simple way to answer it is to pwn the WinRAR licensing scheme to use this pwned/modified WinRAR as freeware. Other purpose? One of the new tought is to make a kinda Portable Version of WinRAR which you can run it without install it to your PC. Other purpose? Are insignificant, like possibility to promote a web site or showing hacking skill by the chance of using LulzSec names..
To make the above objectives happened, the maker pwn the real WinRAR and wrapped it under control of "WinRar v3.71.exe", then making "WinRar v3.71.exe" looks like the real WinRAR by adding icons/stuffs), to avoid "WinRar v3.71.exe" from cracking author using a packer, which widely used by some malwares too. Yes, the way this software made and the way to force it to run in any PC is the problem. Which is a wrong way to start, and this is the REASON why this issue happen from the first place.
Anyway, I run it again and again in my VmWare for hours, and experimenting it a lot, but at this moment I could not see the viral/malware action EXCEPT the stated above. I mean, no rootkits, no file/MBR infections, no network activities, etc.. HOWEVER, 1) The way it was made & it executes as per explained above by using MANY of the malicious software techniques, and 2) Trespassing the security policy of any computer systems; are inviting a so many debates about it. Which I hope to clarify by this writing.
Below I will explain its process screenshot by screenshot:
If you run it, it (it == "WinRar v3.71.exe") will show the start process bars like this:

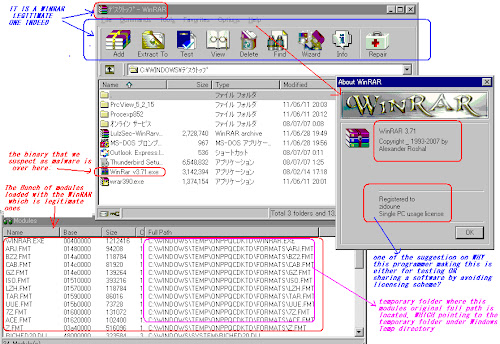
During the process above it will dropped the WinRAR set into the temp directory and it will start the dropped WinRAR program like the below pic. At this point some of the people will think as "a kinda" WinRAR version:
(click to enlarge)
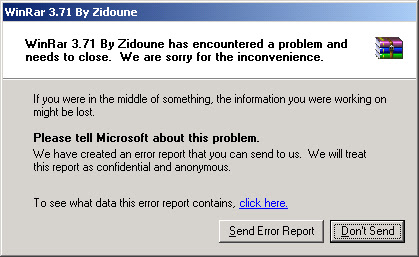
If your system don't fit to the requirement, it will crash and making this error pages like this:
Anyway, you it runs well you will see the actual process detail which will show the "WinRar v3.71.exe" and "WinRAR.exe" processes on it, as a parent and child:
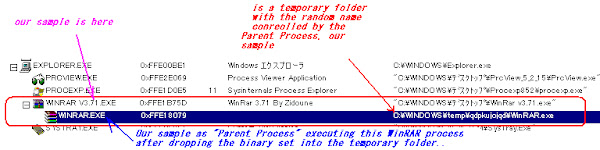
Which the real WinRAR.exe was run from the temporary directory below:
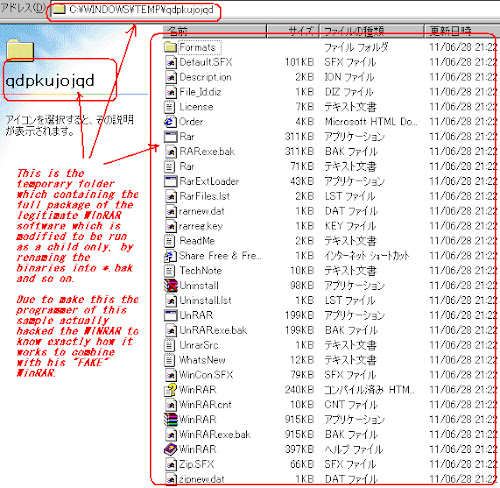
It has the "uninstall" binary included in the dopped directory, I checked its originality, it was using the uninstall script which can be executed to uninstall the WinRAR original components, WHICH can be used for proving which component are hacked packages. So let's executed it :

As you can see above, after the uninstall executed it will erased the original WinRAR set oackages and will leave the hacked ones, these files are the modified ones:

List of files are:
RAR.exe,bak
rarreg.key
UnRAR.exe.bak
WinRAR.cnt
WinRAR.EXE
and.. there is an internet shortcut file called "Share Free & Free All.url" which if you CLICK it you will redirected to a site in south east asia, the redirection process can be traced as followings:
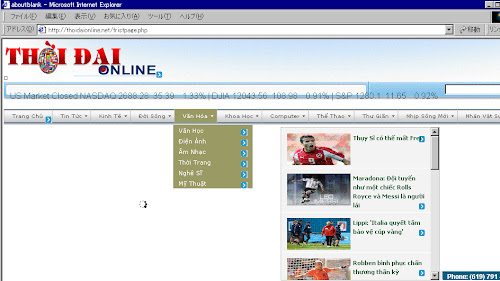
The result of the redirected page is http://thoidaionline.net/fristpage.php as per below screenshot, at this point I was wondering wether the maker is coming from this country..
rarreg.key
UnRAR.exe.bak
WinRAR.cnt
WinRAR.EXE
and.. there is an internet shortcut file called "Share Free & Free All.url" which if you CLICK it you will redirected to a site in south east asia, the redirection process can be traced as followings:
--10:18:33-- http://www.gold4rum.net/
=> `index.html'
Resolving www.gold4rum.net... 74.220.199.24
Connecting to www.gold4rum.net|74.220.199.24|:80... connected.
HTTP request sent, awaiting response... 301 Moved Permanently
Location: http://thoidaionline.net/ [following]
--10:18:33-- http://thoidaionline.net/
=> `index.html'
Resolving thoidaionline.net... 74.220.199.24
Reusing existing connection to www.gold4rum.net:80.
HTTP request sent, awaiting response... 302 Moved Temporarily
Location: fristpage.php [following]
--10:18:34-- http://thoidaionline.net/fristpage.php
=> `fristpage.php'
Reusing existing connection to www.gold4rum.net:80.
HTTP request sent, awaiting response... 200 OK
Length: unspecified [text/html]
[ <=> ] 138,716 162.30K/s
10:18:35 (162.01 KB/s) - `fristpage.php' saved [138716]
=> `index.html'
Resolving www.gold4rum.net... 74.220.199.24
Connecting to www.gold4rum.net|74.220.199.24|:80... connected.
HTTP request sent, awaiting response... 301 Moved Permanently
Location: http://thoidaionline.net/ [following]
--10:18:33-- http://thoidaionline.net/
=> `index.html'
Resolving thoidaionline.net... 74.220.199.24
Reusing existing connection to www.gold4rum.net:80.
HTTP request sent, awaiting response... 302 Moved Temporarily
Location: fristpage.php [following]
--10:18:34-- http://thoidaionline.net/fristpage.php
=> `fristpage.php'
Reusing existing connection to www.gold4rum.net:80.
HTTP request sent, awaiting response... 200 OK
Length: unspecified [text/html]
[ <=> ] 138,716 162.30K/s
10:18:35 (162.01 KB/s) - `fristpage.php' saved [138716]
The result of the redirected page is http://thoidaionline.net/fristpage.php as per below screenshot, at this point I was wondering wether the maker is coming from this country..

Let's check it out in the blacklist service and see what the result of it:

well, red-marked means the domain is blacklisting, while the purple-marked means NOT a good reputation domain.. Interesting.
I tracked down this service for tracing malware on it, destination IP address is located at the below network / location:
IP: 74.220.199.24
*) GEOLOCATION:
Geolocation Information
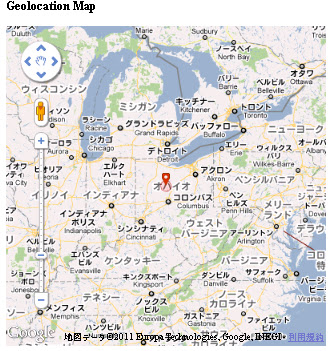
Country: United States us flag
State/Region: Ohio
City: Marion
Latitude: 40.5982
Longitude: -83.1425
Area Code: 740
*) NETWORK:
ASN: 11798
N/W: 74.220.192.0/19
DATA CENTER: ACEDATACENTERS-AS-1
COUNTRY: US
ISP DOMAIN: BLUEHOST.COM
ISP NAME: BLUEHOST INC
*) DOMAIN:
Domain Name: GOLD4RUM.NET
Registrar: SPOT DOMAIN LLC DBA DOMAINSITE.COM
Whois Server: whois.domainsite.com
Referral URL: http://www.domainsite.com
Name Server: NS1.FASTDOMAIN.COM
Name Server: NS2.FASTDOMAIN.COM
Status: clientRenewProhibited
Updated Date: 21-may-2010
Creation Date: 09-aug-2006
Expiration Date: 09-aug-2012
Domain Name: THOIDAIONLINE.NET
Registrar: SPOT DOMAIN LLC DBA DOMAINSITE.COM
Whois Server: whois.domainsite.com
Referral URL: http://www.domainsite.com
Name Server: NS1.FASTDOMAIN.COM
Name Server: NS2.FASTDOMAIN.COM
Status: clientDeleteProhibited
Status: clientRenewProhibited
Status: clientTransferProhibited
Status: clientUpdateProhibited
Updated Date: 21-may-2010
Creation Date: 22-apr-2008
Expiration Date: 22-apr-2013
And at this time I think we can get the peson who can be asked about this matter at the below contacts:
*) REGISTRANT/ADM/TECH/BIILING CONTACT INFO
*) GEOLOCATION:
Geolocation Information

Country: United States us flag
State/Region: Ohio
City: Marion
Latitude: 40.5982
Longitude: -83.1425
Area Code: 740
*) NETWORK:
ASN: 11798
N/W: 74.220.192.0/19
DATA CENTER: ACEDATACENTERS-AS-1
COUNTRY: US
ISP DOMAIN: BLUEHOST.COM
ISP NAME: BLUEHOST INC
*) DOMAIN:
Domain Name: GOLD4RUM.NET
Registrar: SPOT DOMAIN LLC DBA DOMAINSITE.COM
Whois Server: whois.domainsite.com
Referral URL: http://www.domainsite.com
Name Server: NS1.FASTDOMAIN.COM
Name Server: NS2.FASTDOMAIN.COM
Status: clientRenewProhibited
Updated Date: 21-may-2010
Creation Date: 09-aug-2006
Expiration Date: 09-aug-2012
Domain Name: THOIDAIONLINE.NET
Registrar: SPOT DOMAIN LLC DBA DOMAINSITE.COM
Whois Server: whois.domainsite.com
Referral URL: http://www.domainsite.com
Name Server: NS1.FASTDOMAIN.COM
Name Server: NS2.FASTDOMAIN.COM
Status: clientDeleteProhibited
Status: clientRenewProhibited
Status: clientTransferProhibited
Status: clientUpdateProhibited
Updated Date: 21-may-2010
Creation Date: 22-apr-2008
Expiration Date: 22-apr-2013
And at this time I think we can get the peson who can be asked about this matter at the below contacts:
*) REGISTRANT/ADM/TECH/BIILING CONTACT INFO
Thoi Dai Online
Tuan Pham
2725 Menlo Ave
San Diego
CA
92105
US
Phone: +1.6195045509
Email Address: nguyencomp@gmail.com
*) And as cross reference you can check in google and find that mail address and web site contact person is the same:
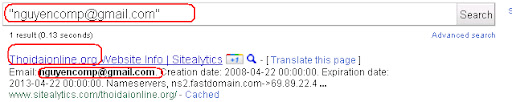
PS: I think after I disclose this, many data will be changed by this malicious software maker..
Tuan Pham
2725 Menlo Ave
San Diego
CA
92105
US
Phone: +1.6195045509
Email Address: nguyencomp@gmail.com
*) And as cross reference you can check in google and find that mail address and web site contact person is the same:

PS: I think after I disclose this, many data will be changed by this malicious software maker..
2. There are so many antivirus detecting this as malware, why?
I can say a long way about this, shortly speaking, this "WinRar v3.71.exe" was made like the malware made (using packer, fake icon, suspicious attributes) and was behave like the malware itself (executing another program in foreign memory, dropping another binary sets, dropping shortcut to internet and changing the browser to make the homepage of it, hidden the installation and erasing all after process ended). Even though this time we cannot find the malware / distruction / infection code inside of it.. I will not surprise if it is made by the malware maker.
Technically, "WinRar v3.71.exe" contains the detection factors belows (Here goes the techies..) :
- The look of "WinRAR" file/icon itself looks lame from beginning..

- using packer(Multi Packer made by Borland Delphi 4.0) which lead to many suspicious points:
- original & actual size of CRC is different, Claimed: 0, Actual: 3163928
- file timestamp was changing to 0x2A425E19 [Fri Jun 19 22:22:17 1992 UTC
- packer made this calls happens:
0x46a24c LoadLibraryA // get DLL
0x46a2a0 GetProcAddress //malloc address to a process
0x46a330 CloseHandle
0x46a170 GetProcAddress
0x46a2a0 GetProcAddress //malloc address to a process
0x46a330 CloseHandle
0x46a170 GetProcAddress
- The way it installed and executing making these hook/calls using much:
0x46a2bc GetFileAttributesA // used for the creating files+process
0x46a31c CreateProcessA
0x46a320 CreateFileA
0x46a5e8 GetKeyboardState // used to wait for response of enter -
0x46a5f4 GetKeyState // key due to popup messages...
0x46a6b8 CallNextHookEx // Used for parent-child process..
0x46a31c CreateProcessA
0x46a320 CreateFileA
0x46a5e8 GetKeyboardState // used to wait for response of enter -
0x46a5f4 GetKeyState // key due to popup messages...
0x46a6b8 CallNextHookEx // Used for parent-child process..
- These loaded DLL and running DLL inviting suspicious looks, especially if you see it deeper to its DLL's hooks/calls ..
- The Read Registry List showing most of the PC sensitive data was read/taken.
- While this software couldn't run and crashed it will showing this windows as per explanied before:
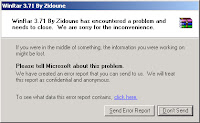
Above pic explanation is: calling the drwtsn32.exe which previously in registry was added by this key: Value Name: [ Debugger ], Value: [ drwtsn32 -p %ld -e %ld -g ], and then executing it together with dwwin.exe C:\WINDOWS\system32\dwwin.exe -x -s 208. Well this operation is a system levels, which was tweaked to run this way. There is a security privilege issue which make this program need to change DEP info to run this, thus, is a sensitive system files executed via foreign execution way. No wondermany scanners and analyst's alerts came up because of only this point.
- The all of above points are also causing suspicious entropy results (I tested with many automation tools in linux), which the way I see it is: the maker made this software moves in a suspicious & malicious way by purpose so this detection also appears. Below is the shell snapshot of those suspicious entropy alerts.
(click to enlarge the picture)
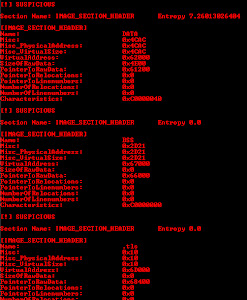
PS: The complete list of the suspicious entropy can be viewed here
- The above factors lead to the Virus Total detection result below:
Malware detected! [26/42] (61.9%)
Win32/Spybot.worm.232373
Trojan/Win32.Buzus.gen, Win32:Trojan-gen
Win32:Trojan-gen, Generic11.RXU
Trojan.Generic.1044496, Trojan.Buzus-3655
W32/Backdoor2.ASHM, TrojWare.Win32.Buzus.~KLO
W32/Backdoor2.ASHM, Trojan.Generic.1044496
PossibleThreat.vw, Trojan.Generic.1044496
Win32.SuspectCrc, TrojanDropper.StartPage.lk
Backdoor, Artemis!2A282A5D8489
Artemis!2A282A5D8489, W32/Suspicious_Gen.DVLE
Trj/CI.A, Trojan.ADH
Trojan.ADH, TROJ_GEN.R4FC3C2
TROJ_GEN.R4FC3C2, Trojan-Dropper.Win32.Agent.cyp
Trojan/Win32.Buzus.gen, Win32:Trojan-gen
Win32:Trojan-gen, Generic11.RXU
Trojan.Generic.1044496, Trojan.Buzus-3655
W32/Backdoor2.ASHM, TrojWare.Win32.Buzus.~KLO
W32/Backdoor2.ASHM, Trojan.Generic.1044496
PossibleThreat.vw, Trojan.Generic.1044496
Win32.SuspectCrc, TrojanDropper.StartPage.lk
Backdoor, Artemis!2A282A5D8489
Artemis!2A282A5D8489, W32/Suspicious_Gen.DVLE
Trj/CI.A, Trojan.ADH
Trojan.ADH, TROJ_GEN.R4FC3C2
TROJ_GEN.R4FC3C2, Trojan-Dropper.Win32.Agent.cyp
The Conclusion:
So, it is up to you to judge wether LulzSec Final Release file was malware or not. I was the one who said it as malware at the first time yet have to admit that no viral code inside of it BUT other than that, it is a purposely made in malicious way. is a kind of file I would like to avoid myself. You can call it a riskware if you want, but THIS IS NEVER BE A GOODWARE. Legitimately is against the licensing agreement of WinRAR software I use and love (hope the person who pwned this can get what he deserved) and this software BREAKS the vital windows security policies w/o warning.
One more thing. One thing that I cannot except is the one who said this software is a False Positive. Since False Positive is a term to be used for a good software/goodware that was honestly made but got mistakenly judged by AntiVirus/Malware scanner as a virus or malware. Our case is not like that, not even close to it, which wehave to be clear about. I used to detect many FP regarding to the Japanese softwares, I am against FP, and fight to correct the situation on daily basis. But regarding to this software, frankly, it deserves to be judged as malicious program.
For your consideration, take a look at the following risk factors too:
1) What if the desitination redirection of shortcut URL file dropped by this malicious software changed at the server side and redirecting users to the malware site instead? This changes can be done at anytime in the server side.
2) What if you use this software and you will get the licensing problem with the WinRAR maker?
3) What if the idea given by this software is taken by the REAL malware maker and remake it in much more malicious way?
2) What if you use this software and you will get the licensing problem with the WinRAR maker?
3) What if the idea given by this software is taken by the REAL malware maker and remake it in much more malicious way?
Please kindly consider above points before judging.
Additionally, if you are a malware analyst or malware researcher, please be free to analyze and judge yourself by downloading the sample stated in this page URL, and kindly post your comment/opinion in the Virus Total here
Thank you for reading.
----
Zero Day Japan
http://0day.jp
Malware Researcher Hendrik ADRIAN
Sponsored by: 株式会社ケイエルジェイテック
Tweet
The Metasploit megaprimer has been re-created with the latest advances and also with a certification: http://securitytube-training.com/certifications/securitytube-metasploit-framework-expert/ Testimonials look good.
返信削除